🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Securing Utilities with Byos
Powering Efficiency and Cyber Resilience

In the era of Industry 4.0, utility providers are embracing digital transformation to improve real-time decision-making, streamline operations, and enhance system performance. Byos provides a scalable solution that enables utilities to securely connect and manage critical assets, ensuring operational efficiency while protecting against cyber threats. For utility providers, this means being able to unify communications across substations, simplify infrastructure, and boost data visibility—all while keeping networks safe, compliant, and efficient.
The Challenges for Utilities
Utility providers face unique security challenges, from legacy equipment with limited protection to complex OT environments where even a single compromised device can lead to widespread disruption or possible downtime. The rapid adoption of digital technologies, combined with proprietary protocols and third-party vendors, increases attack surfaces and complicates security management.
Key Challenges

Legacy Devices and Limited Security
Many critical utility assets operate on legacy systems, making them vulnerable to modern threats.

Dispersed and Isolated Networks
Utility operations and maintenance often span across multiple locations, requiring secure connections for efficient monitoring and control.

Complex Vendor Ecosystems
Multiple third-party vendors introduce additional risks, with each connection representing a potential attack vector.
Introducing the Byos Secure Edge™ Platform
Byos’ platform provides a comprehensive solution with Secure Edge™ isolation of devices within microsegments - preventing lateral movement, and enabling remote access without internet exposure. Byos ensures secure seamless connectivity and centralized control, helping utilities maintain resilient operations.
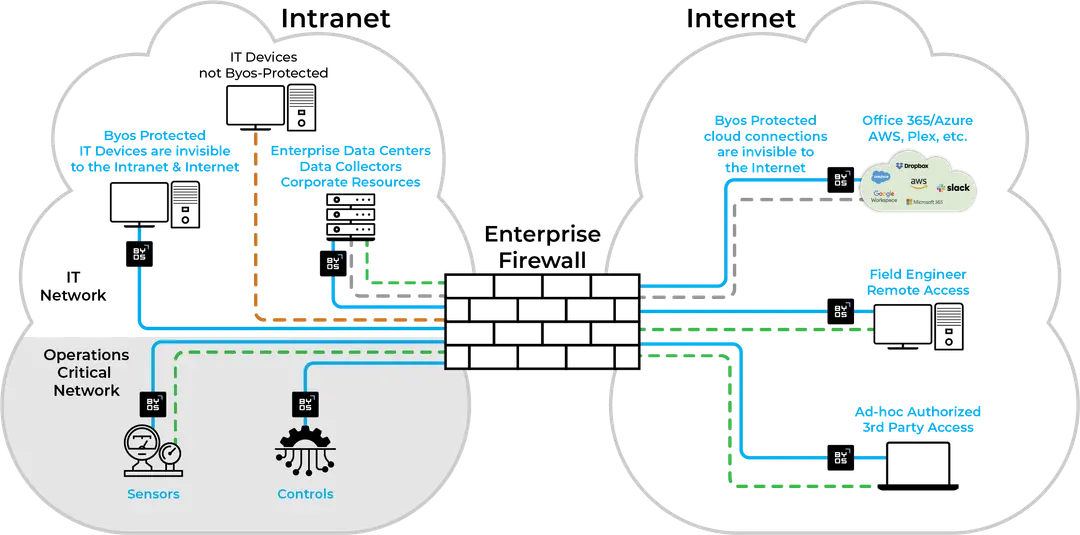
Key Benefits
Simplified Security Management
Byos’ centralized platform allows plant engineers to manage security without IT intervention, reducing complexity and improving response times.

Real-Time Device Visibility and Control
Gain full visibility into all connected devices in your utility network, monitor security status, and enforce policies from a single, centralized interface.

Granular Third-Party Access Control
Limit third-party access to specific devices, timeframes, and geographies, ensuring strict control over who can connect to your network.

How It Works
By isolating devices and preventing lateral movement, Byos’ hardware-enforced microsegmentation platform minimizes the impact of potential breaches, protecting critical infrastructure from any possible widespread disruption. Byos unifies utility substations communications, enabling efficient administration and security through a single platform.
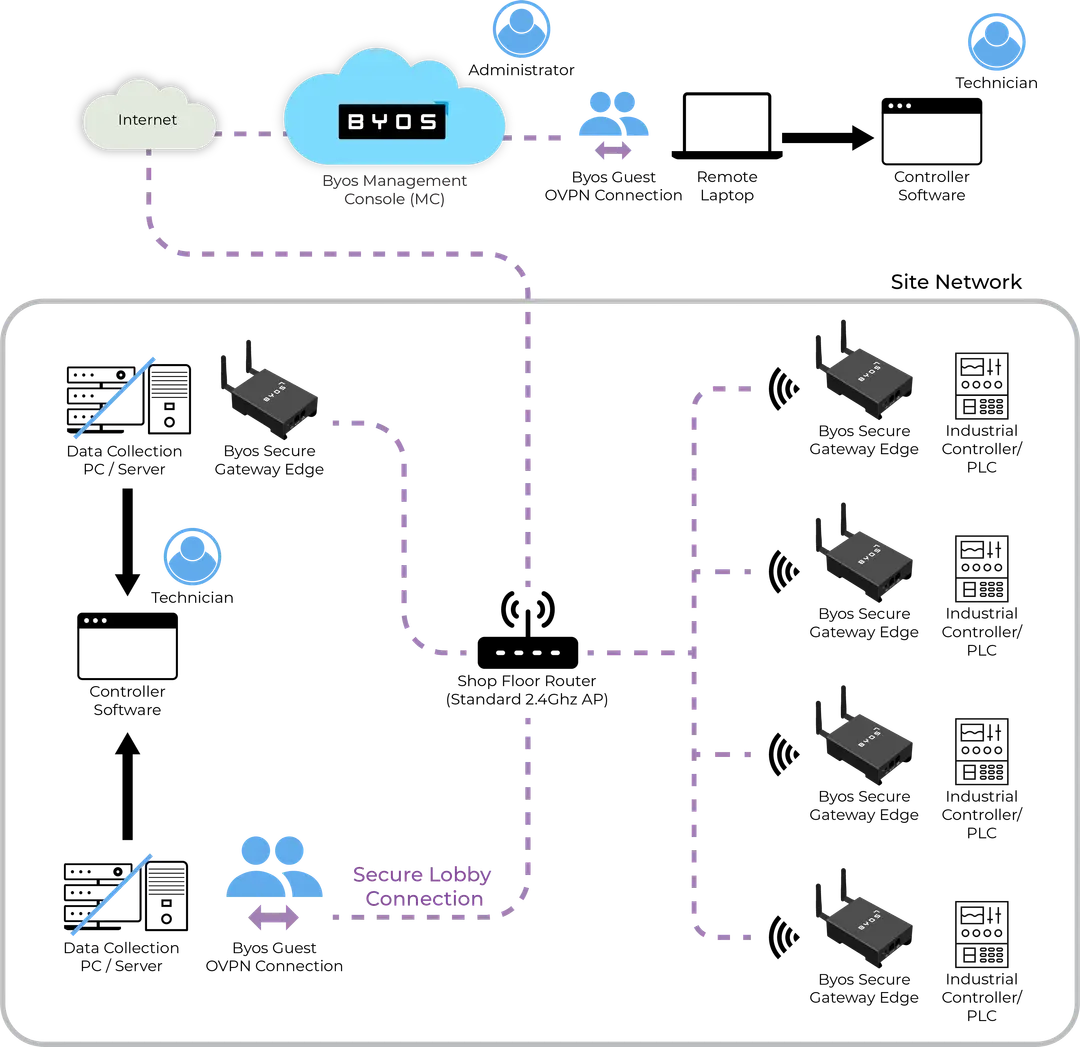
Microsegmentation for Asset Isolation:
Byos isolates each device within a secure microsegment, reducing the attack surface and containing potential threats to a single endpoint.
Private, Encrypted Remote Access
with Byos Secure Lobby™: Enable technicians and vendors to access devices remotely without exposing the network to the internet.
Centralized Management and Policy
Enforcement: Administrators use the Byos Management Console™ to manage and monitor devices across all locations, ensuring consistent security and policy compliance.
Results for Utilities: Why Utility Providers Trust Byos
Plug-and-Play Deployment
Byos integrates seamlessly with existing infrastructure, requiring no network reconfiguration. This simplifies deployment and minimizes operational disruptions.

Reduced System Complexity
Critical infrastructure operations are particularly complex with cybersecurity technologies too often being only partially deployed and being difficult to integrate. Byos’ solution not only simplifies security management and brings “plug-and-play” design, but also eliminates the need for multiple technologies.

Compliance and Risk Mitigation
Byos’ encrypted communications, granular access controls, and auditable security policies helps meet stringent industry regulations and reduce compliance risks.

Business Value

Cost-Effective Modernization for Legacy Systems
Securely connect legacy devices with plug-and-play deployment, eliminate costly replacements, extend the asset life, and improve efficiency through wireless connectivity

Reduced Maintenance and Operational Costs
By enabling secure remote access and troubleshooting, Byos eliminates the need for frequent on-site visits, cutting operational expenses and improving response times.

Operational Continuity and Reliability
Safeguard your key infrastructure, preventing downtime from cyber threats and ensuring smooth, uninterrupted operations across all utility sites.
Get the Byos Utilities Use Case
See a Demo
See a demo by our team and learn how Byos helps secure OT and IT utility environments without compromising operational agility or connectivity, helping providers achieve a balance of both efficiency and security.
FAQs
Platform
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)
