🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Byos Secure Lobby™
For trusted, isolated communications with exposure
Private, Encrypted communications between Endpoints
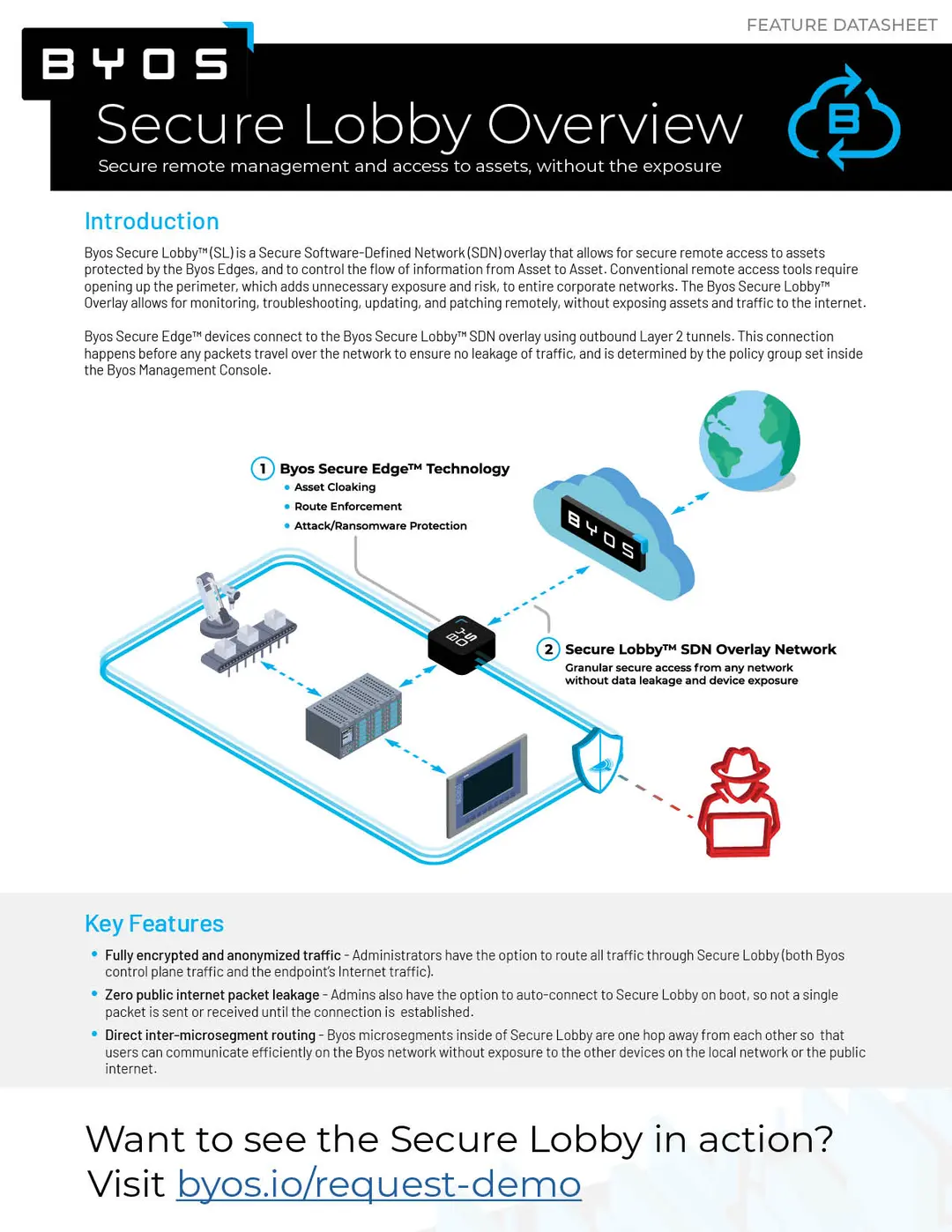
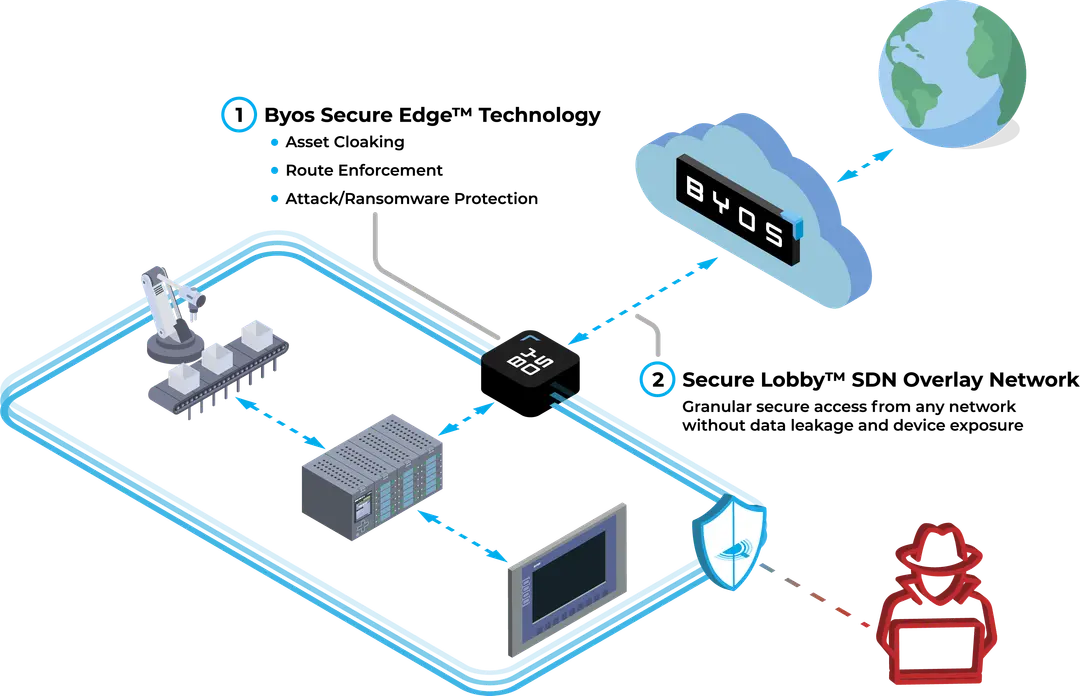
Designed to empower IT and OT teams, Secure Lobby™ Software-Defined Network (SDN) overlay allows secure, controlled access to any device protected by Byos Secure Edge™ technology. Whether you’re managing industrial equipment, healthcare systems, or legacy infrastructure, Secure Lobby™ ensures your data and connection stays private, offering complete peace of mind.
How It Works
Byos Secure Lobby™ establishes a secure SDN overlay through Layer 2 tunnels created by Byos Secure Edge™ devices, encrypting all traffic and isolating assets in private microsegments. Administrators can initiate a Secure Lobby™ connection through the Byos Management Console, enforcing strict access policies that define who can connect, when, and from where. This powerful control over device communications ensures secure, private access across even the most complex networks.
- Initiate Secure Connections: Administrators initiate secure, outbound RSA-encrypted connections to connect devices without perimeter exposure.
- Encrypted Microsegments: Byos isolates devices in encrypted microsegments, allowing secure communication and preventing lateral movement within the network.
- Policy-Driven Access Controls: With granular Layer 3 and 4 access controls, administrators define device permissions, traffic routes, and connection parameters to control device access fully.
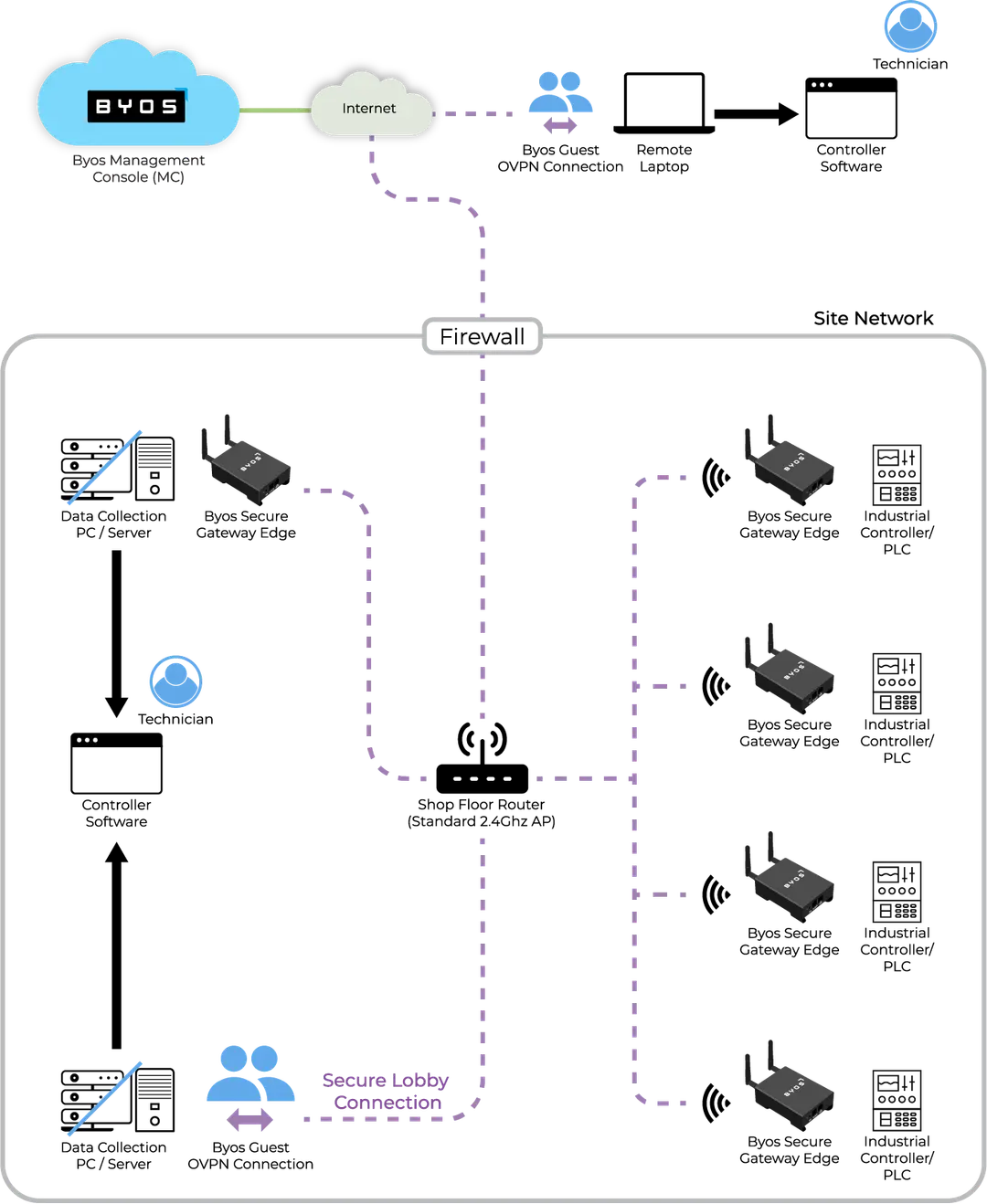
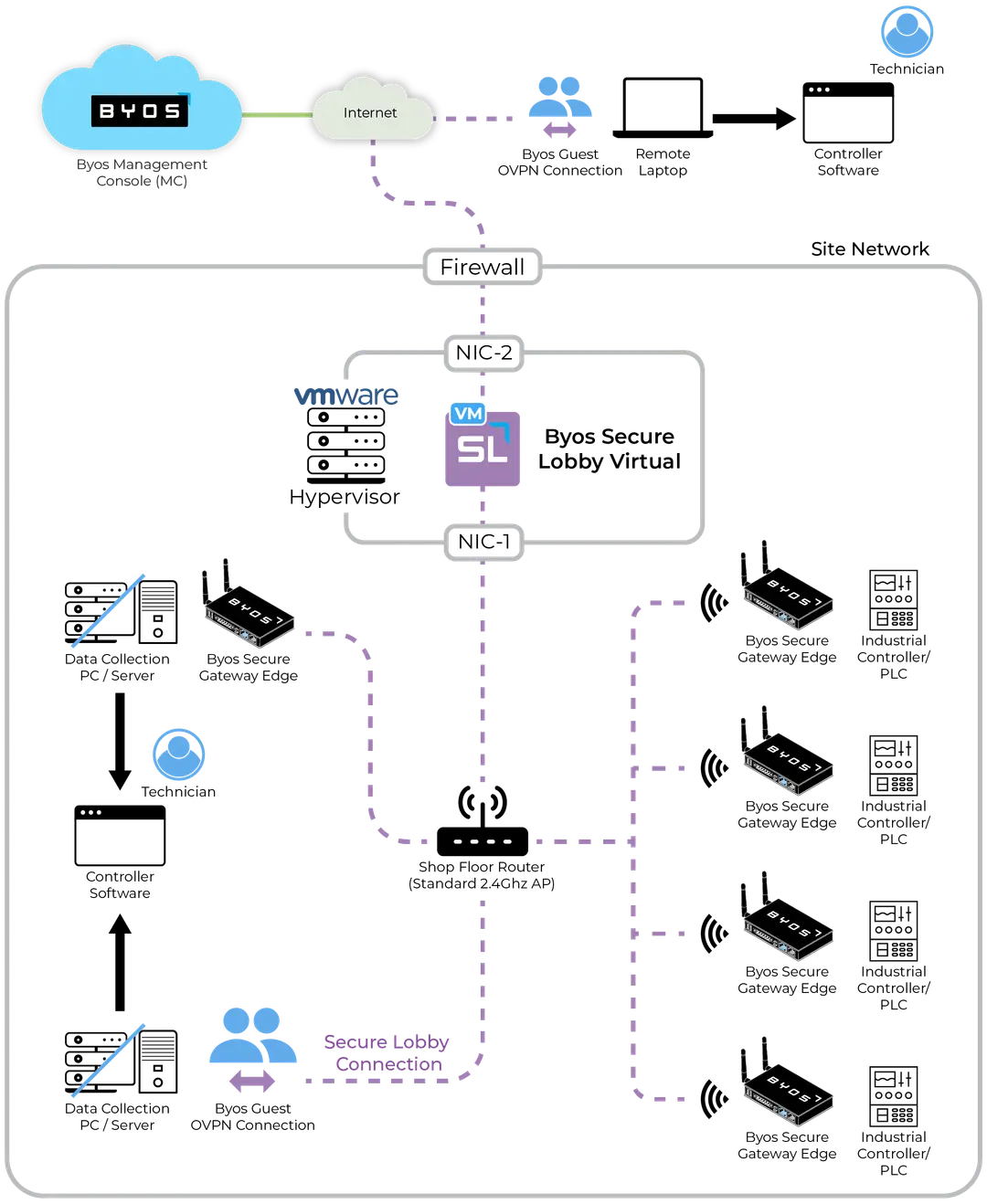
On Premise Deployment
Customers receive their own dedicated Secure Lobby server with flexible deployment options. While Byos manages standard cloud deployments, customers can also choose to self-host their Secure Lobby server on bare-metal infrastructure or within their private cloud environment. The Secure Lobby Server is delivered as a Virtual Machine, ensuring maximum compatibility across platforms.
-
Full Control - On Premise Secure Lobby allows you to control the server and data directly, without exposing the traffic to the internet.
-
Faster Speeds - For data intensive applications, On Prem Secure Lobby provides shorter paths for less latency
-
Local Access - Manage the server locally, hooking up other security tools to monitor the data
Key Benefits
Fully encrypted and anonymized traffic
Administrators have the option to route all traffic through Secure Lobby (both Byos control plane traffic and the endpoint’s Internet traffic). With complete traffic anonymity, your network remains secure and uncompromised.

Zero public internet packet leakage
Secure Lobby™ guarantees that not a single packet is sent or received or transmitted to the public internet until a fully encrypted connection is established, keeping sensitive information completely private.

Direct inter-microsegment routing
Byos microsegments inside of Secure Lobby are one hop away from each other so that users can communicate efficiently on the Byos network without exposure to the other devices on the local network or the public internet.

Benefits of Byos Secure Lobby™ for Corporate and Industrial Networks
Extend Device Life and Security
Securely connect legacy and previously air-gapped devices to a protected network without compromising safety, ensuring long-term asset utility.

Significant Cost Reductions with Secure Remote Troubleshooting
Minimize on-site technician visits and operational disruptions with remote maintenance capabilities, reducing both costs and downtime across critical assets.

Non-Intrusive Deployment
With Byos, there’s no need for complex reconfiguration. Secure Lobby™ seamlessly integrates into your existing infrastructure, ensuring protection without network perimeter risks.

Experience the Ease and Security of Private Access with Byos Secure Lobby™
Byos Secure Lobby™ enables efficient, private, and secure remote access without compromising on data protection. For industries with strict security needs, Secure Lobby™ delivers comprehensive control, connectivity, and peace of mind in a fully encrypted SDN overlay. With Byos Secure Lobby™ , you gain all the benefits of remote access while keeping your critical assets invisible to external threats.
FAQs
Platform
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)