🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Byos Secure Edge™
A CSfC Retransmission Device for remote laptop protection against ransomware and lateral movement.

Challenges
Retransmission devices, as required by the NSA's Commercial Solutions for Classified (CSfC), are clunky, expensive, and don't offer anything other than connectivity out - there's no centralize control and no attack prevention.
Key benefits

Small, Plug-and-Play device
No cables, no software

Flexible Implementation
Internal and External Retransmission devices for different use cases

CSfC compliant
Meets requirements for MA CP 2.6 11.8 Retransmission and 11.9 for Hardware Isolation
Byos Secure Networking Platform
Byos Secure Edge™ makes endpoints invisible on the network through hardware-based Edge microsegmentation, providing protection from ransomware and lateral movement.

Embedded Edge™
A M.2 secure networking card for the WWAN slot inside laptops
Endpoint Edge™
A small, external USB-c device for laptops and tablets

Gateway Edge™
An IoT Gateway for stationary assets like workstations, PLCs, Servers, etc.
Byos Centralized Control Plane
Manage and control access across a diverse fleet of assets, protected by Byos Secure Edge™ devices

Management Console™
Admin Interface

Secure Lobby™
Secure SDN Overlay
Core Capabilities

Agentless Protection
Microsegmentation provides network security at the edge, reducing the attack surface

Enhanced Visibility
Centralized fleet-wide visibility and threat management of networking assets

Granular Control
Seamless provisioning and secure access to any endpoint, regardless of the network
Key Features
Asset Isolation
Each device has an isolated microsegment, keeping assets invisible on local networks and preventing discovery, fingerprinting, and unauthorized access.

Protection Against Advanced Threats
Enforce Zero Trust principles with least-privilege access, defending against lateral movement, ransomware, spoofing, DoS, and man-in-the-middle attacks.

OS-Independent Security
Byos Secure Edge™ operates independently of the OS, protecting against bypass and stealth attacks targeting the operating system.

How It Works
Deploying the patented Byos Secure Edge Platform is effortless. Simply plug in the Secure Endpoint Edge™ to your device, or connect to your IT/IoT/OT systems through the Secure Gateway Edge™ or Secure Embedded Edge™ device. You'll be able to manage traffic with precision firewalls through the Management Console™, and encrypt all communication, ensuring only authorized data flows through your network with the Byos Secure Lobby™.
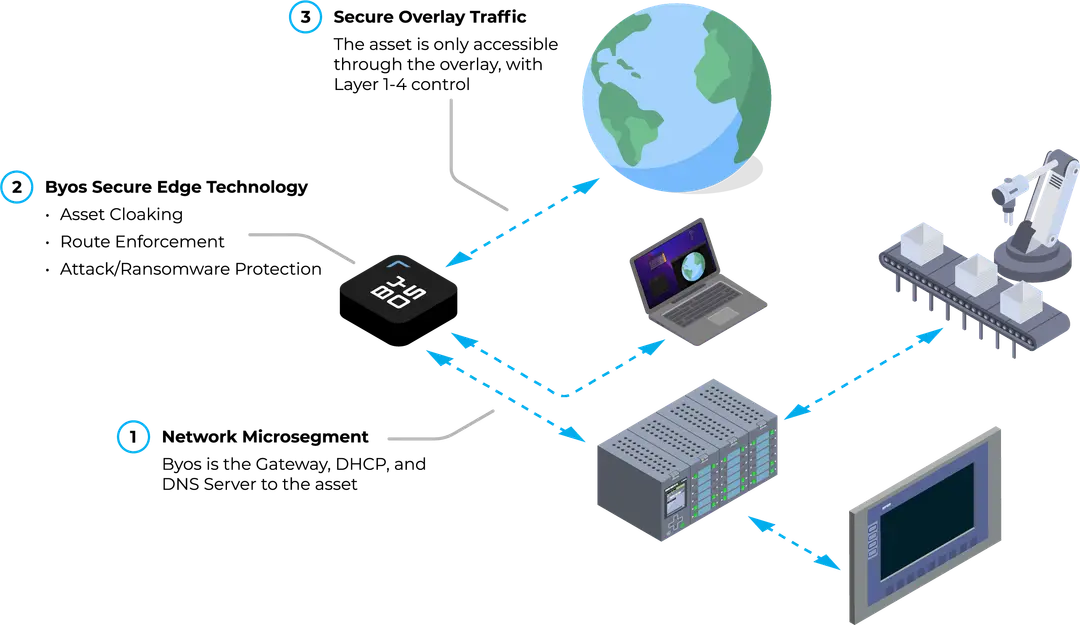
With Edge microsegmentation, the patented Byos Secure Edge Platform isolates assets and prevents any lateral movement - ensuring your assets remain invisible on the network, and visible only when you want to them to be.
Get the Byos CSfC Use Case
FAQs
Platform
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)
