🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Securing Machine Data Capture with Byos
Protecting Critical OT Insights

For modern industries, machine data capture is the backbone of operational efficiency, enabling real-time insights, predictive maintenance, and optimized production. However, as data flows increase across interconnected devices, so does the risk of cyber threats. By isolating endpoints and applying Zero Trust principles, Byos Secure Edge™ platform allows OT teams to monitor and manage data safely, ensuring device-level protection without compromising network integrity.
The Challenge
Machine data capture involves collecting vast amounts of data from critical OT assets such as sensors, controllers, and industrial equipment. While the benefits of machine data capture in OT are obvious, the risks of ransomware, downtime, and exposure of networks to cyber threats are growing:
- Legacy System Vulnerabilities: Older devices lack built-in security, making them prone to unauthorized access and exploitation.
- Lateral Movement Risks: A compromised device can allow attackers to spread across the network, endangering critical systems and data.
- Remote Accessibility Without Exposure: Enabling secure, remote access to geographically dispersed devices without risking public internet exposure is complex.
Introducing Byos
Protecting Legacy and Proprietary OT Devices
Byos is designed to be able to connect with older legacy assets and OT machinery, isolating them within secure microsegments, allowing for safe data capture without risking exposure.

Continuous, Secure Data Collection Across All Sites
Byos provides secure data capture for remote and dispersed assets, giving administrators centralized real-time insights through Byos Management Console™ across multiple sites without risk.

Eliminating Risk of Lateral Movement
Each OT device is isolated within its own secure microsegment, containing any potential threat within the device or microsegment, ensuring it doesn’t spread and vastly reducing the threat of ransomware.

How It Works
Byos combines advanced hardware-enforced edge microsegmentation, Zero Trust policy enforcement, and encrypted communications to protect every device involved in machine data capture.
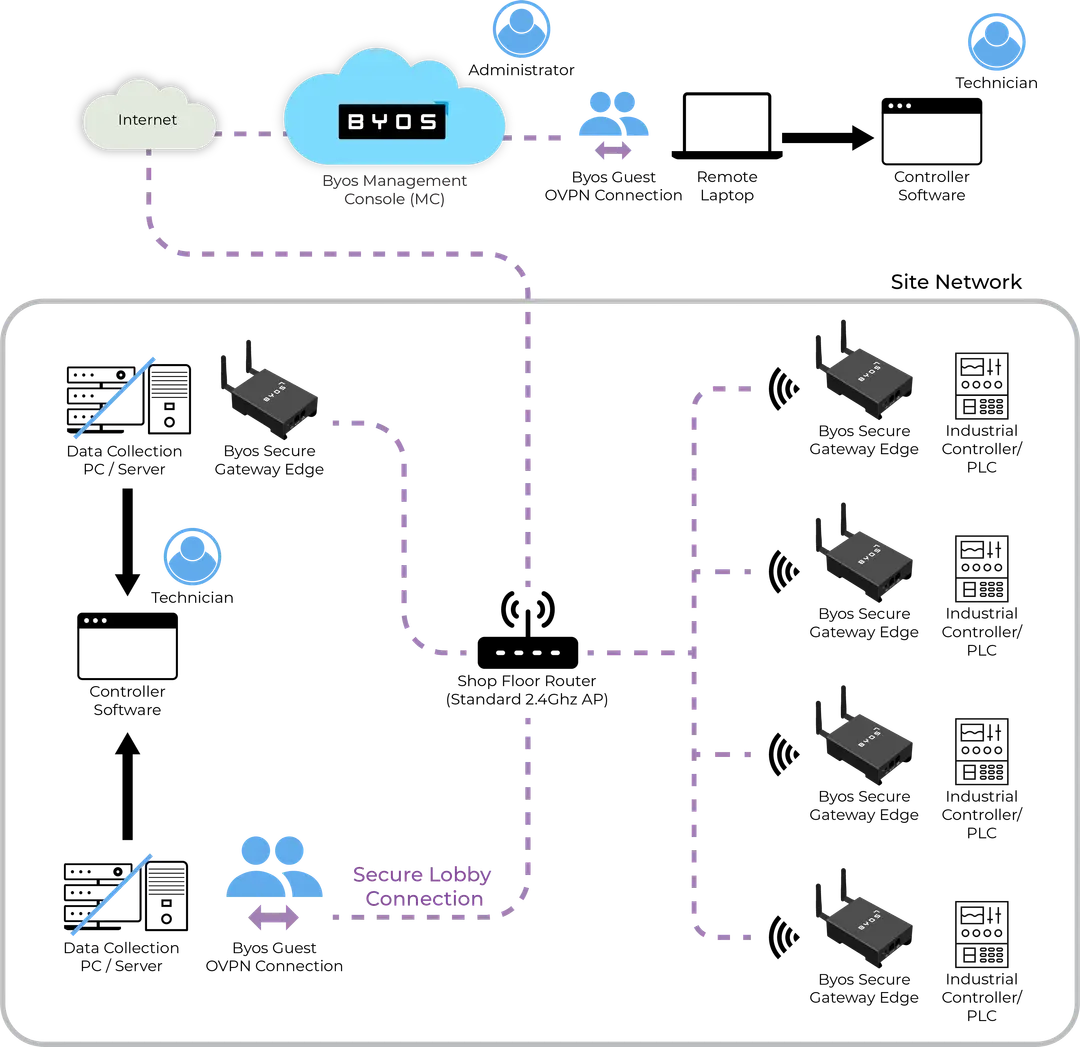
- Byos-protected devices connect through the Byos Secure Lobby™, a secure SDN overlay that enables safe, private access for real-time monitoring and remote maintenance
- Byos encrypts all data collected from machine endpoints, ensuring compliance and protecting sensitive information.
- Centralized control through the Byos Management Console™ provides administrators with visibility, control, and confidence, allowing you to capture data securely from anywhere.
Key Benefits
Maximized Device Lifespan and Operational Efficiency
Protect legacy systems with Byos, allowing older devices to capture data securely, extending their useful life without costly upgrades.

Reduced Operational Complexity and Costs
Set policies and manage access controls for each device from a single, centralized interface. Enable secure, remote monitoring of OT devices, reducing maintenance costs and the need for on-site visits.

Minimal Operational Disruption
Byos’ plug-and-play platform is designed to connect with both OT assets and IT networks, allowing easy integration with your existing networks, without requiring any major network reconfigurations or downtime.

Unlock the Power of Machine Data Capture Without Compromising Security
Byos ensures your organization can securely capture and utilize critical machine data without risking device exposure. Our Secure Edge™ Platform provides easy, scalable protection, allowing you to focus on operational excellence and efficiency with confidence. Discover how Byos’ microsegmentation platform can give you a more proactive and comprehensive approach to securing your OT environment.
FAQs
Platform
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)