🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
About Byos
Transforming Security at the Edge.
Our Story
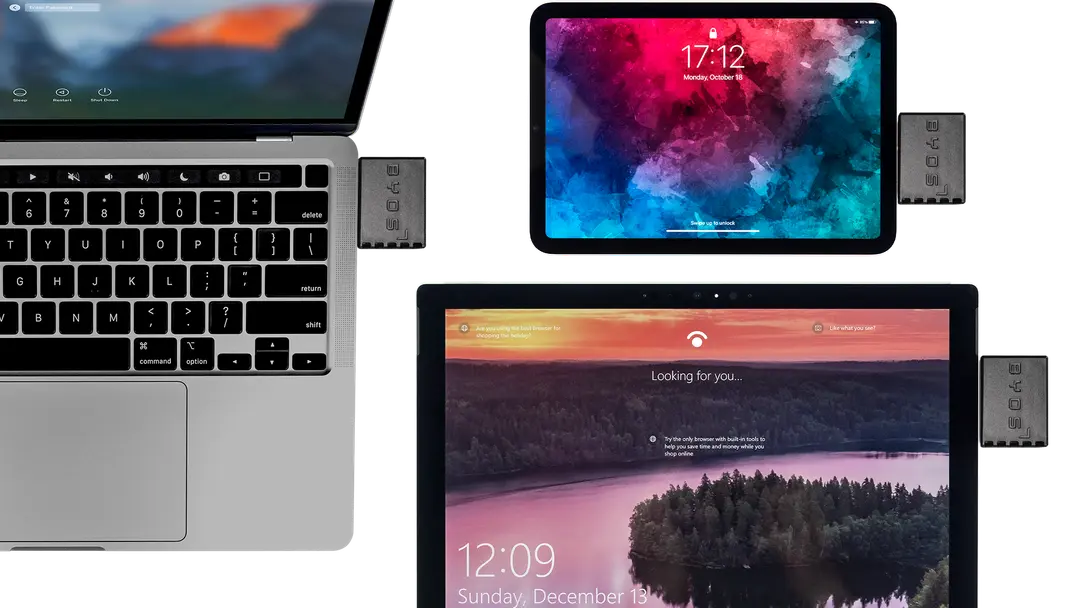
The Byos microsegmentation platform provides Edge networking protection, asset invisibility & isolation, and granular secure access to resources without data leakage nor device exposure. Byos was built for Zero Trust networking and is inherently compatible with all sorts of existing devices and network environments. This not only brings dramatic reduction in risk - but it unlocks new opportunities for greater efficiencies, productivity and data aggregation for optimal performance and savings.
Byos serves customers across the fields of Critical Infrastructure, Manufacturing, Defense and Government, Healthcare, Energy, and Financial Services - securing everything from plant floor machinery, to EV charging stations, to individual employee laptops.
Our Mission & Vision
Empower organizations to secure their most critical assets by providing simple, robust, and scalable edge security solutions.
A new Internet where all assets are invisible and no device can communicate without authorization.
Our Technology
Byos Secure Edge Microsegmentation Platform
The patented Byos Secure Edge platform combines Zero Trust architecture and microsegmentation to protect devices and networks at the edge.
Endpoint Edge™
Protects laptops, tablets, and mobile devices with an agentless, plug-and-play solution designed for remote workforces.

Gateway Edge™
Safeguards OT systems, legacy devices, and critical infrastructure by preventing lateral movement and ensuring secure data flow.

Embedded Edge™
Secures laptops as a secure networking card being embedded inside the device, providing network security at the edge

Cluster Edge™
Secures datacenters, deployed seamlessly into the server rack, creating secure microsegments for devices, apps and customer data without extra hardware
Use Cases
Request a demo to see how Byos would work in your environment
Meet our Advisory Board
John’s exceptional career spans 26 years with the FBI, including as Deputy Director. Post-9/11, John led key initiatives in counterterrorism and national security operations. Later, being nominated as TSA Administrator by President Obama and unanimously confirmed by the U.S. Senate, he introduced new risk-based security approaches, reshaping airport security for millions. In 2010, Pistole was awarded the National Intelligence Distinguished Service Medal by the Office of Director of National Intelligence (ODNI).

As CIO of the U.S. Air Force (USAF), General Bender oversaw a $17B IT portfolio, spearheading modern cybersecurity practices, introducing key roles like CISO and CDO in the DoD. At USAF, he also led communications training and global deployment efforts for 21,000 personnel in Baghdad. As SVP at Leidos, his leadership grew revenues from $10B to $15B. He has held advisory roles with major organizations, shaping the intersection of defense and technology.

Dave Lewis has over 30 years of industry experience, with extensive experience in IT security operations and management, including including roles at Duo Security, Akamai, and Cisco. Dave is currently the Global Advisory CISO for 1Password. He is also the founder of the security site Liquidmatrix Security Digest & podcast. Lewis also serves on the advisory board for the Black Hat Sector Security Conference in Canada, the CFP review board for 44CON in the UK and as an advisor to Sightline Security.

Jeff brings over 25 years of experience in IT, security, and engineering across both private and public sectors. As the former CTO at the FBI, he led to the delivery of a groundbreaking case management system, significantly enhancing the agency’s threat awareness capabilities. His leadership at the FBI is recognized as a case study in exceptional agile development processes. As former VP at United States Postal Service (USPS), he led over 1200 employees, governance of the IT platforms, and championed operational resilience and efficiency.

With over 25 years of experience, Bob’s journey began in 1999, building encryption systems and pioneering network data flows to detect cyber threats. As the first Security Monitoring lead at Verizon Wireless, he spearheaded multi-million-dollar projects that safeguarded over 100 million customers as well as tens of thousands of Verizon's employees. At the time, Bob oversaw one of North America’s largest botnet monitoring programs. A sought-after keynote speaker, Bob has presented at the IMF, CES, and across Europe, sharing insights with global leaders.

Erik has built global information security programs from the ground up as CISO for American Axle & Manufacturing and as Head of Information Security at Penske Automotive Group, while championing security as a game changing differentiator in driving business results. Erik's extensive expertise includes being President and CEO of CXO Xchange, holding a bachelor’s and master’s degree in Information Assurance from Walsh College, Executive MBA from the University of Michigan, and being certified as a CISSP, GPEN, GWAPT and CCSK.

As a distinguished former FBI Senior Executive, Thomas brings over three decades of leadership at the highest levels of federal law enforcement and national security. As Assistant Director of the FBI’s Criminal Justice Information Services (CJIS) Division, he led 2,800+ personnel and oversaw the development of multi-billion-dollar biometric and real-time data-sharing programs across different law enforcement agencies, including Next Generation Identification and N-DEx. Today, he advises across the homeland security and public safety ecosystem, bringing unmatched leadership in interoperability, identity intelligence, and secure information exchange.

Jim brings over four decades of leadership in government and industry, including 18 years as a U.S. federal senior executive. As Acting Administrator of the U.S. General Services Administration and its first Federal Acquisition Service Commissioner, he oversaw $55B+ in annual procurement and led the agency’s 2008–2009 Presidential transition. At the U.S. Department of Homeland Security, Jim served as the first Director of the US-VISIT program, implementing post-9/11 biometric entry systems that transformed border security. He has been recognized with multiple honors, including two Presidential Rank Awards and four Federal Computer Week FED100 Awards.

Why Trust Us?
Security is in our DNA and engrained in everything we do. Our commitment to security is reflected in the products we build and the way we operate, all for the protection and integrity of the customer.

Data Privacy
We do not read Secure Edge traffic data and we also never sell or rent personal information to third parties.

End-to-End Encryption
The communications between the Secure Edge and Management Console are encrypted end-to-end.

Cloud Security
Our servers are compliant with Cloud Security Alliance standards, further protecting you against vulnerabilities.

In-Device Processing
All security processing is done locally within the Secure Edge, independent of cloud servers, reducing your exposure and protecting your data.

Multi-layer Protection
The Secure Edge has multiple layers of protection built in, including both Hardware and Software security mechanisms.

Continual Testing
We perform testing at all product stages, including SSDLC, internal and 3rd-party pen tests, and offer an open bug bounty program.
FIPS Validated

Byos Cryptographic Module is FIPS 140-2 Validated. Visit the NIST CMVP website for more details - Certificate #4964
Built in the USA

Byos Secure Edge™ hardware has a proprietary hardware board that is manufactured in the USA, with a certified supply chain of components and a certified chain of custody of software, assuring the product does not contain hidden backdoors.
You can learn more about our Product Security, Secure Software Procedures, Cloud Security, Bug Bounty Program, and more.
Channel Partners

Carahsoft Technology Corp. is The Trusted Government IT Solutions Provider ®, supporting Public Sector organizations across Federal, State and Local Government, Education and Healthcare. Visit us at www.carahsoft.com

Converge Technology Solutions Corp. is a services-led, software-enabled, IT & Cloud Solutions provider focused on delivering industry-leading solutions. Visit us at: https://convergetp.com/our-story/cbi/

With over 30 years of experience in commercial and Federal IT, FCN provides infrastructure hardware and software solutions tailored to your organization. Discover more at: https://fcnit.com/
Explore our extensive roster of Channel Partners. Become one today too!
Certifications
Contact Us
Let’s work together to secure your organization. Whether you have questions, want to request a demo, or explore partnership opportunities with Byos, we’re here to help.
Platform
Use Cases (Industry)
Use Cases (Application)
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)







