🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
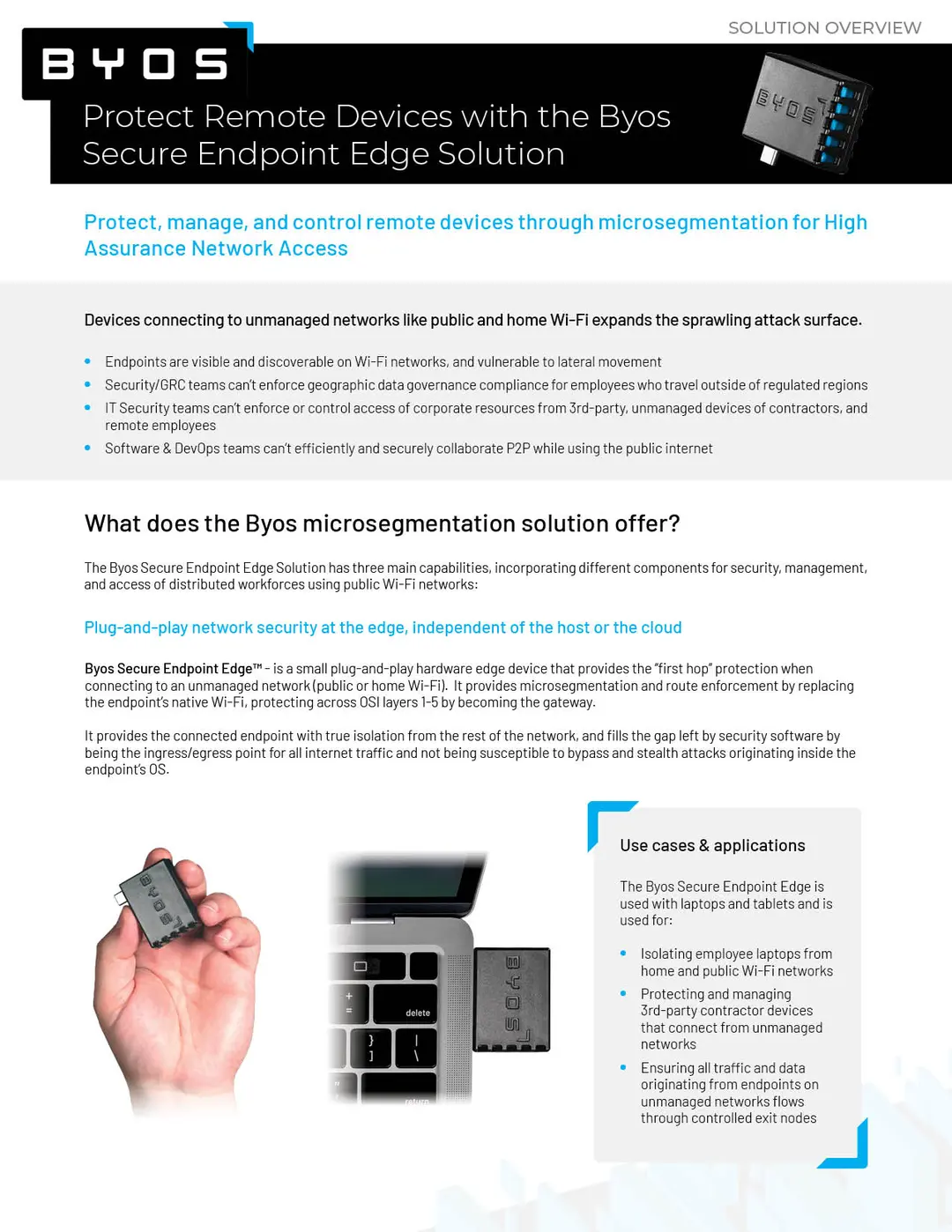
Byos Secure Endpoint Edge
A small plug-and-play External Retransmission device providing "first hop" protection on untrusted Wi-Fi networks.

Microsegmentation for Remote Workers
Byos Secure Endpoint Edge™ protects your laptop by isolating it from the network, making you invisible at a coffee shop, airport, or conference. It eliminates the attack surface and minimizes the blast radius of any attack trying to leverage lateral movement.
Attackers can't bypass it because it's independent from the OS, making it compliant with NSA's CSfC requirements.
Benefits and ROI
Microsegmentation at the Edge
Each device is isolated in a microsegment, blocking lateral movement and protecting against ransomware and unauthorized access.

Asset Isolation
With Byos assets are completely invisible on local networks, preventing discovery, fingerprinting, and unauthorized access attempts.

Plug-and-Play Deployment
Byos is agentless, connecting via USB-C, requiring no software or network changes, ensuring fast, non-intrusive deployment.

Core Capabilities
From a Security Perspective, Byos has three unique differentiators:

Inbound Network Attack Protection:
- "First-hop" protection across OSI Layers 1-5 through Hardware-enforced Isolation
- Obfuscating the protected device to be effectively invisible on the network

Outbound Traffic Protection and Control:
- Network Access Control (NAC)
- Route enforcement
- Traffic anonymization through layer 4+ data encapsulation and exit node enforcement

Centralized Management:
- Policy-driven access control per microsegment
- Byos-enforced IAM Conditional Authorization
- Secure remote access without endpoint exposure
Why was it created?
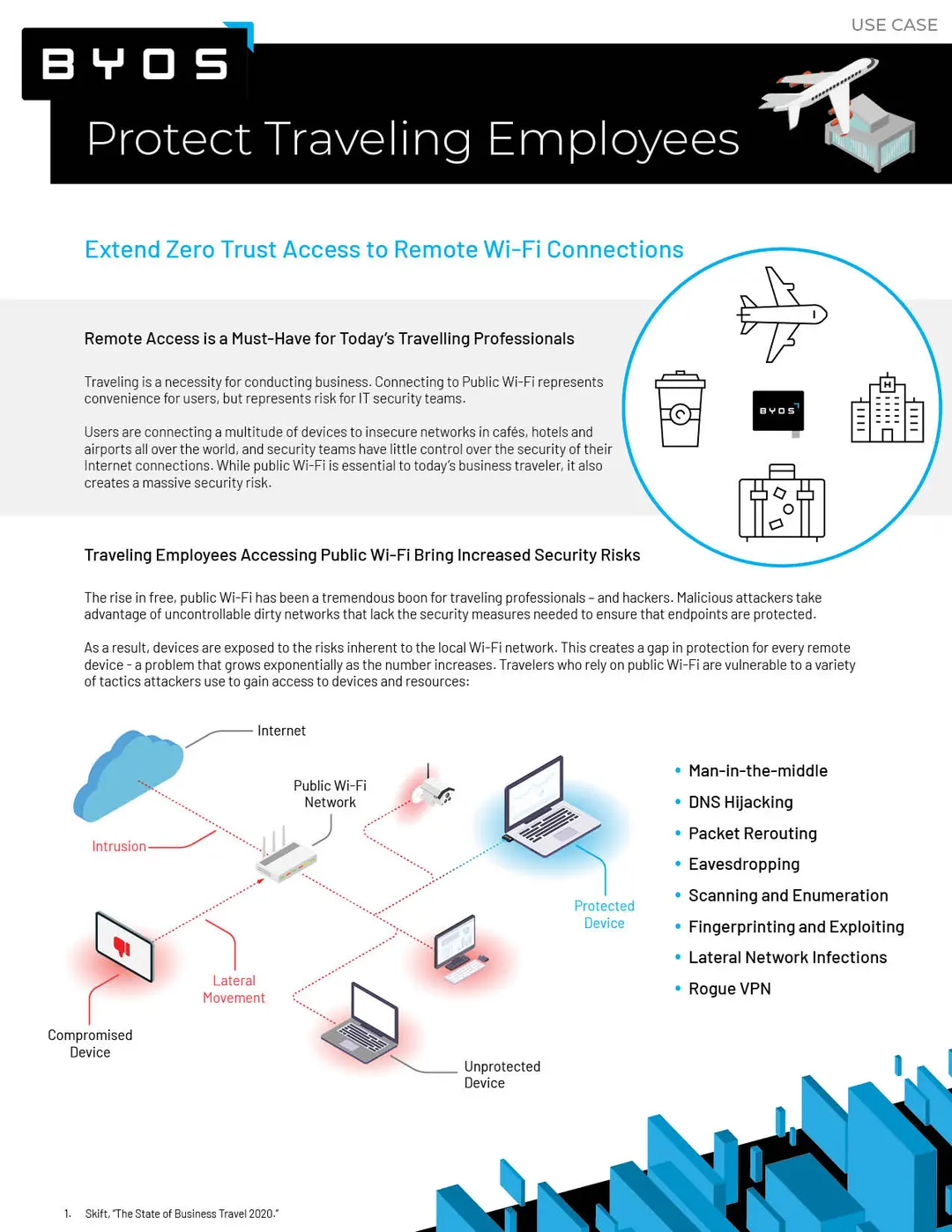
- Vulnerability on Public/ Home Wi-Fi Networks
- Bypass of OS-Level Security Solutions
- Lateral Movement Across Networks
Traditional endpoint security tools can't fully protect against untrusted Wi-Fi face threats like eavesdropping and spoofing.
OS-based security tools can be bypassed, but the Secure Endpoint Edge™ remains independent to protect against stealth attacks.
Byos isolates devices with microsegmentation, preventing attackers from moving laterally through the network.
Byos Secure Networking Platform - How It Works
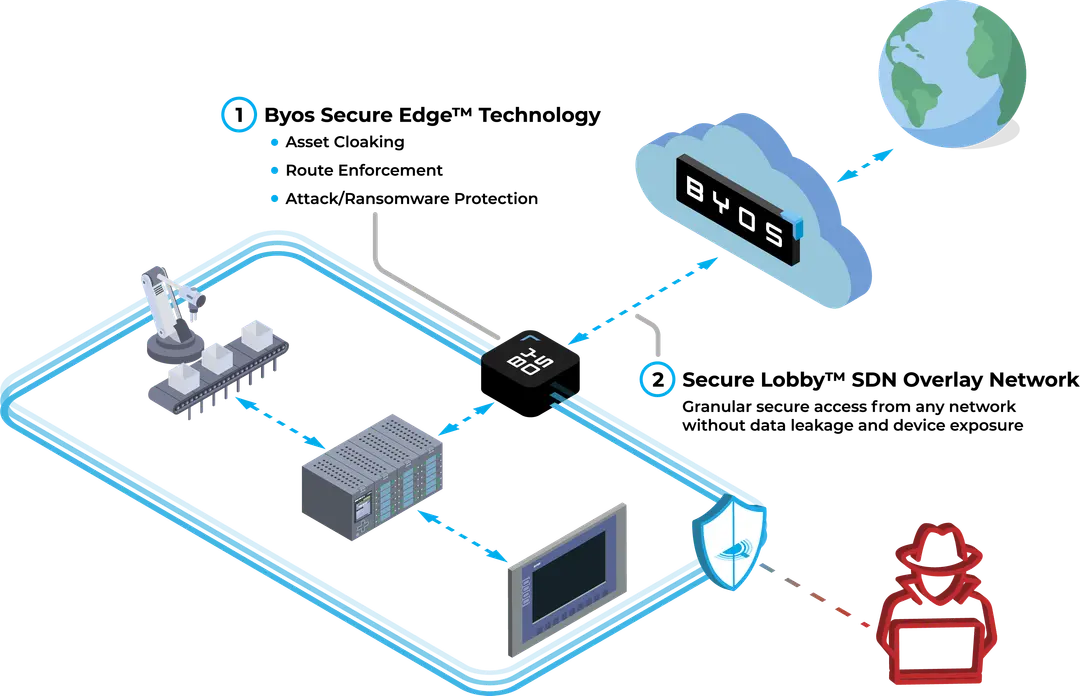
Byos Secure Lobby™ - the Data Plane
Our Software-Defined Network (SDN) overlay creates a secure communication channel between your Secure Edge™ devices. Manage your entire fleet remotely without exposing sensitive assets to the internet.
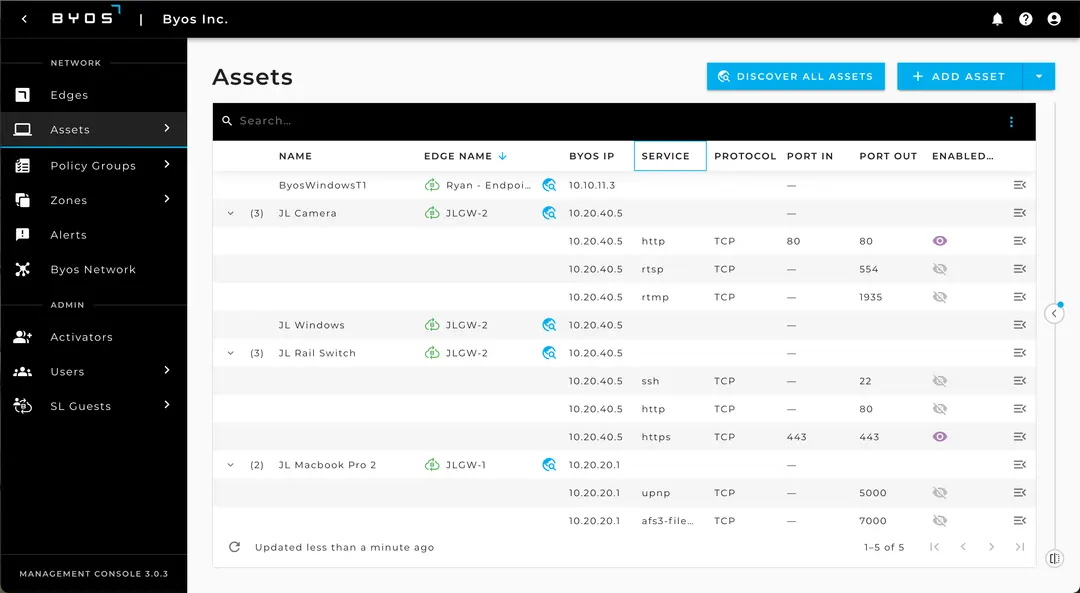
Byos Management Console - the Control Plane
Manage your entire fleet of Byos Secure Edge devices from a single, powerful console. Push security policies instantly and maintain complete visibility across your network edge.
Where does Byos Secure Endpoint Edge fit in the security stack?
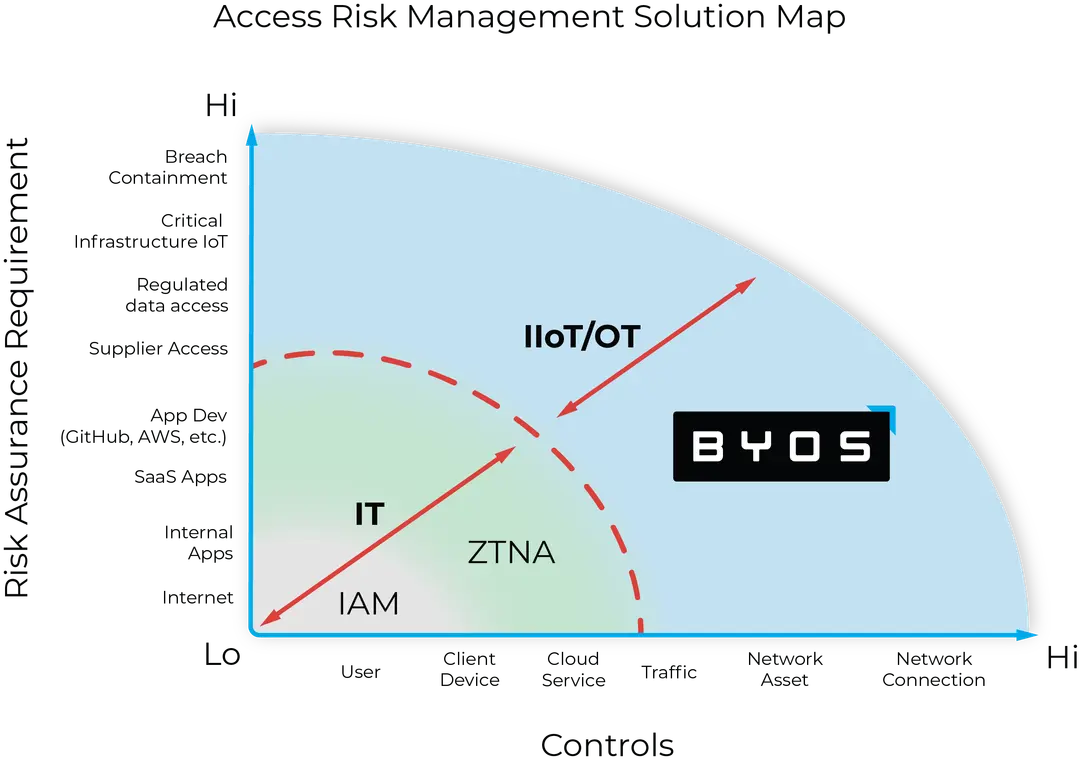
Byos is a new layer of protection in the security stack called Edge Microsegmentation; it protects against these network attacks and contains lateral movement while allowing administrators to manage and control remote endpoints. This type of solution falls in a new category called High Assurance Network Access (HANA)
Why are existing technologies not enough?
- Software-based endpoint protections installed on the OS can be bypassed/evaded.
- Perimeter-based protections cannot protect individual endpoints on the network before an attacker gains a foothold and propagates.
- Getting centralized runtime visibility into the active sessions of distributed endpoints is cumbersome with current tools.
Byos Secure Endpoint Edge Use Cases
Key Use Case: Remote Work
As more employees and executives work remotely, connecting via insecure public and home Wi-Fi networks, organizations face increased risk. Byos works right out of the box, securing laptops and tablets, with microsegmentation and hardware-based isolation.
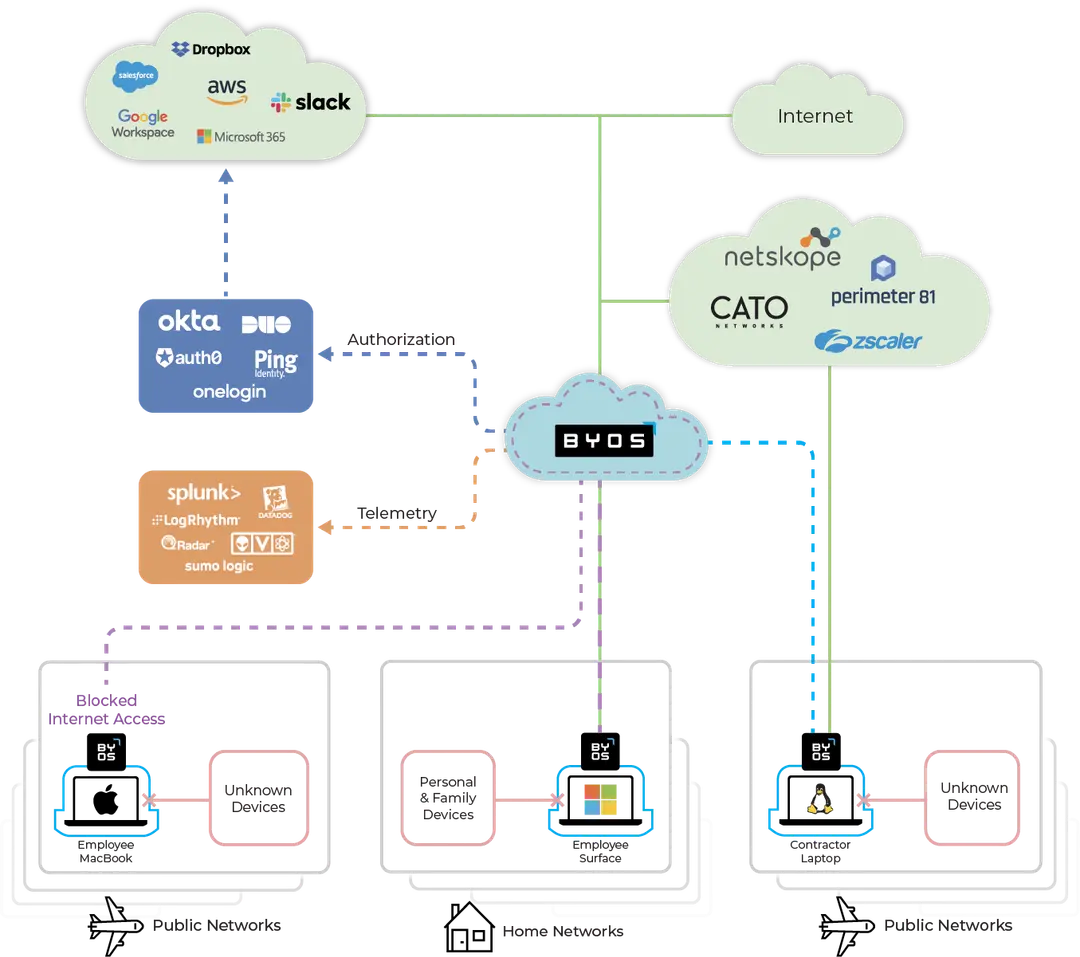
- Protects employee laptops from threats on home or public Wi-Fi.
- Isolates third-party contractor devices connecting from unmanaged networks
- Enforces control over all traffic from unmanaged networks through secure exit nodes
FIPS Validated

Byos Cryptographic Module is FIPS 140-2 Validated. Visit the NIST CMVP website for more details - Certificate #4964
FAQs
Request a demo to see how Byos would work in your environment
Platform
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)