🚀 New Byos Secure Embedded Edge in pre-order! Join the waitlist
Enhancing Security and Control: Third-Party Remote Access Strategies for Critical Infrastructure Networks
Operational Technology | Remote Access
October 20th, 2023

With third-party access, security teams face the challenge of making decisions about who, what, and how external partners, vendors, or contractors requiring network access for collaboration or service provisioning, will get it. VPNs have been the staple of Remote Access security, but networks have grown more complex and so too have the threat vectors. This article will explore some differences between Cloud and On-prem resources, and considerations about different approaches and technologies.
Jump to section:
Different Approaches for Cloud vs. On-Prem Accessed Resources
Considerations of secure, controlled access
Alternatives to VPNs for Third-Party Access
Drawbacks to Technologies that Provide 3rd Party Access Capabilities in OT environment
A New Approach: Benefits of Isolating Third-Party Access
Allowing Third Parties into your network with Byos
Different Approaches for Cloud vs. On-Prem Accessed Resources
Cloud resources generally benefit from built-in security measures due to their public-facing nature, so this blog addresses the challenges associated with on-premise network security. On-premises assets traditionally rely on a complex set of perimeter, network, application, and endpoint protections, as well as incorporating network segmentation, access controls, detection systems, vulnerability management, and security awareness training. Because of the multifaceted nature of most corporate networks, allowing access to enterprise assets by third-parties isn’t as straightforward as it should be. There are often many different ways of achieving remote access, but these different approaches often create a trade off decision between security and convenience.
Considerations of secure, controlled access
There are lots of technologies that simply allow third-parties to have access to the network, but ensuring that access is secure and controlled is another. There are several considerations to be thought of when selecting remote access solutions for highly critical assets inside of networks:
- Ensure the attack surface is minimized and protecting against inbound lateral movement and network attacks
- Ability to control the level of access to the underlying assets across multiple OSI layers
- Minimizing the “blast radius” in the event of an infection and protection of outbound lateral movement
For additional understanding the deep technical aspects of mitigating these considerations, refer to these articles:
- Preventing Attackers from Gaining Initial Access to Your Network
- Limiting the Blast Radius - Preventing Lateral Movement is Absolutely Critical
- Zero Trust, Industrial IoT, Operational Technology, Remote Access
Alternatives to VPNs for Third-Party Access
When it comes to remote access in OT, there are several alternatives to both traditional and hardware VPNs, each with its own benefits and drawbacks. Hardware VPNs provide a dedicated device for secure remote access, offering enhanced security through hardware-based encryption and authentication. But, their limitations lie in security, visibility and control.
Unidirectional gateways / Data Diodes offer a one-way flow of data between devices, providing protection against unauthorized access. However, they present limitations in terms of data transfer options and compatibility with complex protocols. Their primary drawback is the lack of bidirectional communication, which can restrict certain applications or require additional configurations for necessary interactions. Additionally, the complexity of deployment and management can pose challenges, requiring careful configuration and ongoing monitoring to ensure proper functionality and secure data transmission.
ZTNA (Zero Trust Network Access) is gaining popularity as an alternative approach to secure remote access in IT. Elements of ZTNA are not optimal for OT because almost all ZTNA vendors require an agent to fully implement their solutions, which eliminates the compatibility with legacy and unmanaged devices. The primary objection to ZTNA for OT lies in the complexity of implementation, requiring significant planning and coordination to seamlessly integrate with existing network infrastructure and applications.
In evaluating alternatives to VPNs in OT environments, organizations should carefully assess their specific requirements, considering factors such as scalability, level of expertise & number of resources required to administer, and the complexity and timeframes for implementation. It is crucial to strike a balance between security, usability, and operational efficiency to establish strong and effective third-party controls.
Drawbacks to Technologies that Provide 3rd Party Access Capabilities in OT environments
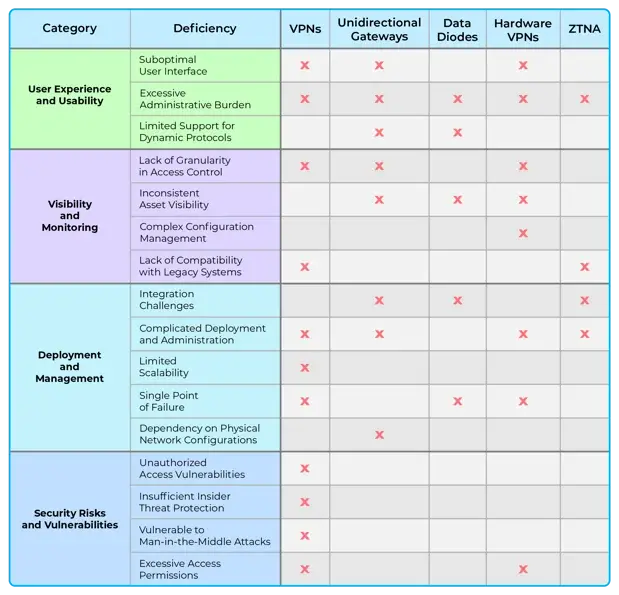
Among the alternatives used by organizations to address remote access for third parties in OT environments, the reality is that each comes with a variety of different limitations and drawbacks. The table below lays out a comparison among these technologies in terms of their limitations with regards to security, practicality, visibility and control - and thus the challenges one would face with implementing each of these technologies.
As a result of these limitations, organizations typically find themselves with new difficulties in terms of ease-of-access and inefficiencies or become straddled with increasingly complex setups to try and make up for these drawbacks. These approaches also often fail to account for the differences in the OT environment compared to IT, leaving gaps in the overall security posture, areas which still can be exploited by threat actors, as well as other tradeoffs in order to provide network access to third-parties. OT specific network security technologies have been created to address the challenges and limitations of these traditional technologies, centered around the idea of isolating the devices from the network - to provide maximum control over communication between devices and prevent the spread of attacks should any device be compromised.
A New Approach: Benefits of Isolating Third-Party Access
At Byos, we have taken this different approach to securing remote access, which involves a few core principles:
- Physically isolating assets from their local network so they are no longer exposed to inbound and outbound networking attacks. By tightly controlling communication between two devices, making their session invisible to all other devices on the network or the internet, while isolating them from any compromised device on the network, the risk of a ransomware attack from infected 3rd party devices is greatly reduced. The attack surface is eliminated.
- Removing remote access from happening on the actual underlying corporate network by creating an Overlay network that facilitates granular and controlled access control to resources within the assets. The Secure Lobby™ overlay approach also brings improved operational efficiency, by enabling communication isolation without disrupting the existing infrastructure, simplifying network management.
- Making it plug and play, legacy compatible, and easy to deploy and manage. Being able to accommodate older technology, allows organizations to leverage their existing investments. This eliminates the need for costly hardware upgrades or replacements, reducing expenses and minimizing disruptions during the transition period.
Allowing Third Parties into your network with Byos
To give a third party access to your assets on-prem, Administrators can create Guests within the Byos Overlay network.
- Guests are Non-Secure Edge Device entities which are given a Byos IP and able to unidirectionally access specific Zones within the Overlay (Layer 3 access control).
- When a Guest is given access to the Byos Network of protected assets. The third-party devices don’t have overly broad access to the underlying LAN network - they only have access to the Assets and Resources that the Admin has enabled (Layer 2 and 4 access controls), and there is no VPN infrastructure to manage. Guests can be given temporary access, and scheduled to expire automatically, and access can be killed at the click of a button.
To read more about the Byos Solution and How It Works for enabling third party access, read the Securing Industrial Control Networks use case
Conclusion
The two fastest growing cybersecurity threats are the susceptibility of OT and the focus that attackers have on supply chain security. Combine those threats with the risks of third-party access into OT, this has increased the priority of executives in manufacturing and critical infrastructure to address those concerns. If you would like to learn more about the latest state-of-the-art OT security technologies that address third-party access, reach out to Byos to speak with an expert.
Platform
Patented Technology. © Byos Inc. - Ashburn, VA. - All rights reserved. Byos Secure Edge™ hardware is manufactured in the USA, with a certified supply chain of components. FIPS 140-2 Validated (#4946)