The Byos Secure Gateway Edge
Built for protecting entire fleets of IoT devices, the Byos Secure Gateway Edge™ protects any type of connected device, providing microsegmentation.
As IoT continues to grow, so do system vulnerabilities
IoT devices are used as an entry point into the larger corporate networks, where the most valuable data resides. Legacy IoT devices such as servers, modems, PLCs, controllers, and networked medical devices are especially vulnerable as attack methods increase in sophistication. The lack of IoT device management capabilities also contributes to challenges, including the absence of built-in security monitoring and update management capabilities.

Get started with the Byos Secure Gateway Edge Overview
What Byos is solving for customers
Protection
Microsegmentation provides network security at the edge, reducing the attack surface
Visibility
Centralized fleet-wide visibility and threat management of networking assets
Control
Seamless provisioning and secure access to any endpoint, regardless of the network
Remote Access without compromising on Security
Are you curious about how organizations with different types of devices in networks they don’t control are managing and servicing endpoints remotely?
The Byos Secure Lobby™ facilitates secure access without breaking isolation.
Modes of Operation
The Secure Gateway Edge can be used in a number of different use cases and applications

Ethernet-mode for Legacy
and Wired Devices
Client-mode to connect to a pre-existing Wi-Fi Network
Features & Benefits
-
Plug-and-play Implementation
TCP/IP compatible so no agent or software installation is required on the host device
-
Zero Touch Deployment
Secure Gateway Edges are automatically enrolled in fleet for immediate security and ease of setup -
Reduced Attack Surface
Secure Gateway Edge has a crypto coprocessor, encrypted filesystem, signed binaries, and secure boot -
Legacy OS Protection
Technology-agnostic, working with any device regardless of operating system, model, or age
-
Improved Security
Multi-layered protection with software security mechanisms across OSI Model layers 1-5 -
Reduced Field Service Time
Secure over-the-air updates to both the Secure Gateway Edge and host device firmware and software -
Flexible Implementation
Suitable for both wired and wireless-connected IoT devices
Industries
Because of its plug and play nature and zero touch deployment, our technology is suitable across a multitude of industries. It helps to secure legacy IT infrastructure without needing to alter the legacy endpoint OS nor changing the local network configuration.
Electric Utilities

Facilities Management
Oil & Gas

Manufacturing

Healthcare

Smart Cities

Water

Food & Beverage

Chemicals

Automotive
Logistics

Mining
Applications
The Byos Secure Gateway Edge™ can be deployed with any endpoint that speaks TCP/IP, making it endpoint agnostic.

Medical
Devices

POS
Devices

Industrial Controllers

Legacy
Servers
Security
Cameras
IoT
Devices

Desktop Workstations

Networking Devices
Key Feature: Byos Secure Lobby
Secure Lobby™ allows for secure remote access to IoT devices protected by the Byos Secure Gateway Edge™. Conventional remote access tools require opening up the perimeter, which adds unnecessary exposure risk to entire corporate networks; Secure Lobby™ allows for monitoring, troubleshooting, updating, and patching remotely, without exposing internal endpoints to the internet.

The Secure Lobby™ creates a secure connection between the Secure Gateway Edge™ and the Byos Management Console™ using an outbound connection, originating from inside of the corporate network perimeter, as to not interfere with local network configurations. This saves both Network Administrators and Service Technicians time when servicing Byos-protected endpoints remotely.
Additional Challenges being solved with Byos
Securing devices on insecure public and private Wi-Fi networks
Reducing risk of 3rd-party access to endpoints in the network
Enforcing security and compliance for legacy and IoT devices
By leveraging endpoint microsegmentation through hardware-enforced isolation, Byos gives IT and security teams the confidence to protect devices against network threats by minimizing the attack surface and protecting against remote code execution exploits.
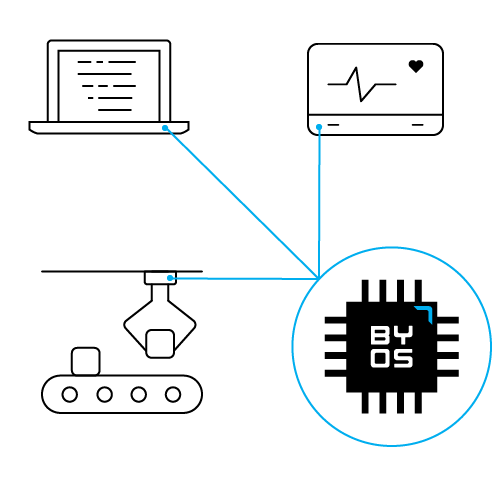
If an alternative attack vector compromises a device, the Byos Secure Gateway Edge™ provides threat containment within the compromised device, preventing lateral network infections from spreading, and preventing ransomware and Denial-of-Service attacks from rendering devices inoperable.
Robust Network Security Protection
The Byos Secure Gateway Edge™ protects against:
Infiltration
Prevention
The Secure Gateway Edge detects changes in packet routing to the Internet and takes the necessary actions to prevent any data leakage.
Eavesdropping
Prevention
The Secure Gateway Edge maintains direct and confidential communications with the network gateway without allowing the poisoning of routing tables.
Attack
Prevention
The Secure Gateway Edge runs an internal security service to detect directed threats and block fingerprinting, enumeration, DoS and exploit attacks.
Controlled
Access
Byos runs a bi-directional firewall, offering incoming and outgoing access control based on country-based and protocol-based traffic, restricting specific domain names, IP addresses and ports.
Private DNS
Queries
The Secure Gateway Edge runs an in-device encrypted DNS server to prevent DNS hijacking and preserve the confidentiality of the user’s browsing data.
Traffic Volume
Control
The Secure Gateway Edge detects exponential changes in network traffic volume often triggered by hidden malware running on the user’s device.