Microsegmentation
Why Microsegmenation Is The Future of Network Security
Network security is in the middle of a complete overhaul. Once the default, perimeter-based security models are giving way to security solutions like microsegmentation that adhere to Zero Trust principles. The natural successor to basic network segmentation, microsegmentation breaks the entire network down to its least divisible components — its endpoints — and provides robust protection and threat mitigation for each component.
The rise of this approach is timely considering the explosion of cyber threats seen over the past few years. The annual number of ransomware attacks reached 304 million in 2020, 120 million more than in 2017. Experts identified 270,000 new malware variants in 2020, up by 120,000 from the year before. And, as the threat landscape has expanded, so has the corporate network: The rapid adoption of smart devices has made this cyber territory almost as hard to define as it is to protect. Given these challenges, many are looking to deploy microsegmentation: a newer, more robust network security technology. Ready to learn more? Contact us today.
Microsegmentation Adoption Rates
What Are Microsegmentation Adoption Rates Across Industries?
Byos surveyed 100 cybersecurity leaders and experts to get an in-depth, data-driven understanding of the adoption of microsegmentation practices across various industries. Their answers indicate that the approach is becoming the new standard for network security:
- Microsegmentation Dominates: 83% of cybersecurity leaders told us that they had already implemented some form of microsegmentation.
- Universal Adoption on the Horizon: 65% of organizations that had not adopted reported that microsegmentation was on the implementation roadmap.
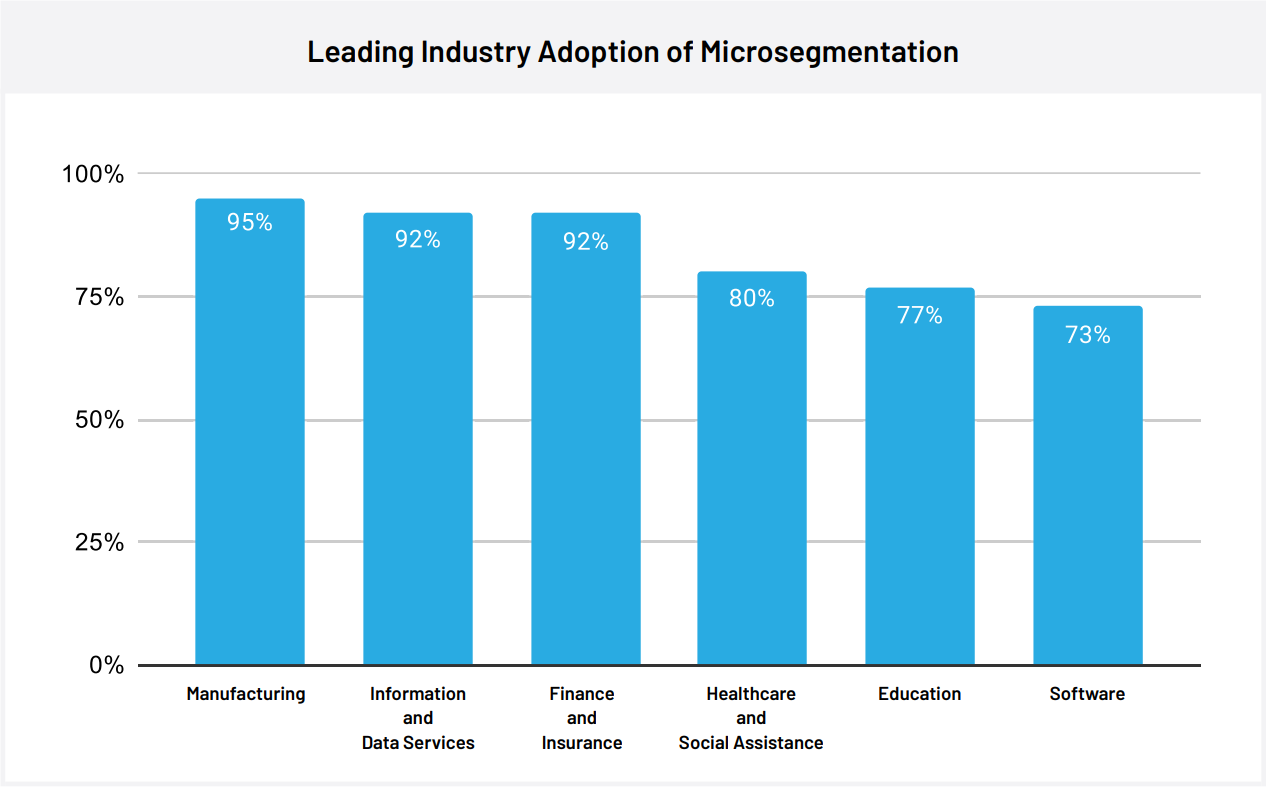
- Manufacturing Leads All Industries: 95% of the manufacturing industry has adopted microsegmentation.
- Tech Close Behind: 92% of the information/data services industry and 73% of the software industry has adopted microsegmentation.
- Finance Embraces Microsegmentation: 92% of the finance and insurance industry has adopted microsegmentation.
- Education Keeping Pace: 77% of the education industry has adopted microsegmentation.
- The Adoption Laggards: Less than 30% of the telecommunications and electronics industries have adopted microsegmentation.
Microsegmentation Benefits
What Are the Benefits of Microsegmentation?
Microsegmenation’s rapid adoption is likely fueled by the overwhelmingly positive reputation the network security model has among practitioners:
- Top Performing Approach: 92% of cybersecurity leaders believe microsegmentation is a more practical and efficient way of improving overall network security than the alternatives.
- Zero Trust Enablement: 88% of cybersecurity leaders believe microsegmentation is essential to achieving Zero Trust network security.
- Critical for IoT Protection: 93% of cybersecurity leaders believe microsegmentation is integral for IoT security.
- Attack Surface Reduction: 89% of cybersecurity leaders believe microsegmentation can effectively minimize an organization’s attack surface.
- Lateral Movement Prevention: 89% of cybersecurity leaders generally agree that microsegmentation helps prevent lateral movement and mitigate network threats more effectively than perimeter-based network security.
- Better Policy Management: 88% of cybersecurity leaders believe microsegmentation helps ensure efficient and effective security policy management.
- Simplified Compliance: 89% of cybersecurity leaders believe microsegmentation can streamline challenges associated with regulatory compliance.
Microsegmentation Adoption Motivations
What’s Driving Organizations to Implement Microsegmentation?
What has those on the fence thinking about implementing microsegmentation? More than anything, cybersecurity leaders want to adopt this approach because they feel it will provide more robust protection against a dangerous threat landscape and increasing network sprawl.
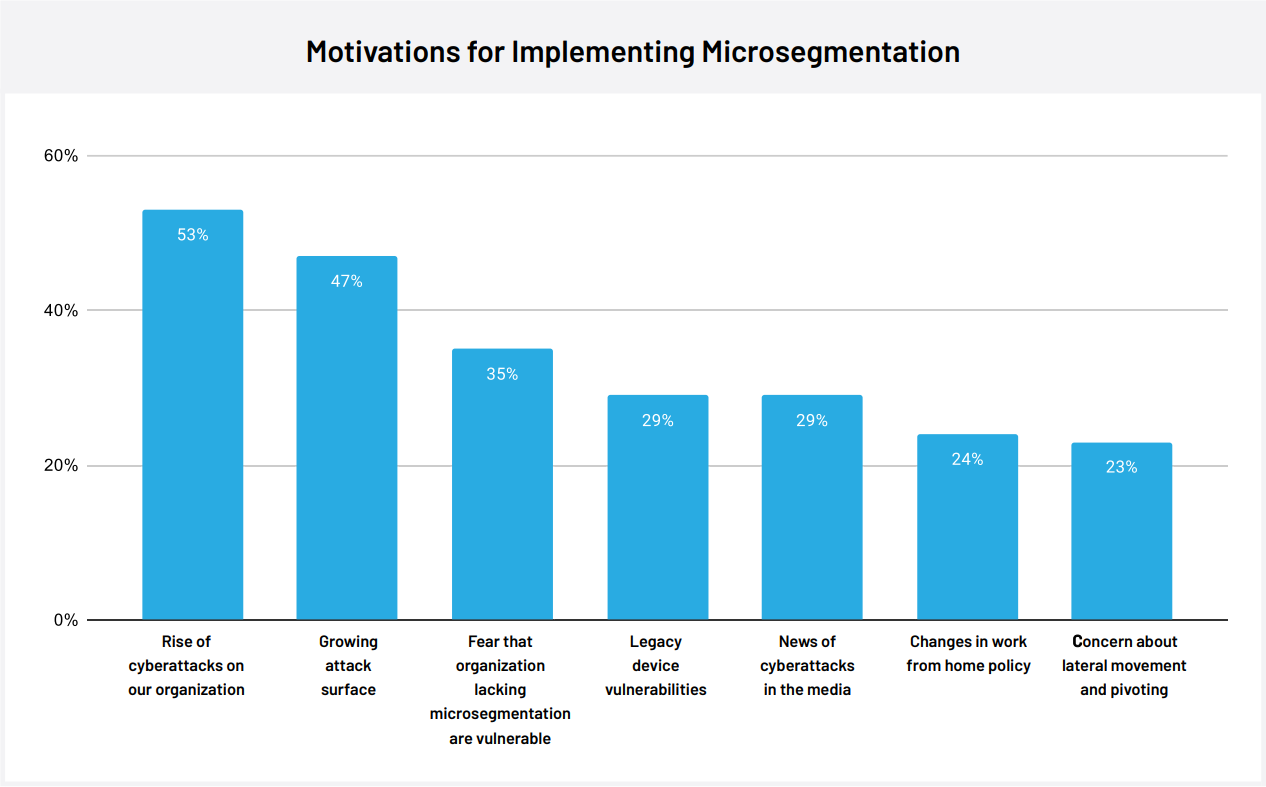
- Increasing Threats: 53% of cybersecurity leaders are considering microsegmentation because their organization is experiencing rising numbers of cyberattacks.
- Larger Attack Surface: 47% of cybersecurity leaders are considering microsegmentation because of their growing attack surface.
- Vulnerability Mitigation: 35% of cybersecurity leaders are considering microsegmentation because they worry that they are leaving themselves vulnerable to compromise without it.
- Legacy Device Protection: 29% of cybersecurity leaders are considering microsegmentation to keep their outdated hardware secure.
- Rising Incident Reports: 29% of cybersecurity leaders are considering microsegmentation because of news of cyberattacks in the media.
- Remote Work Shift: 24% of cybersecurity leaders are considering microsegmentation because of work from home policy changes.
- Lateral Movement Prevention: 23% of cybersecurity leaders are considering microsegmentation because of concerns about lateral movement and pivoting.
Microsegmentation Features
What Are The Top Microsegmentation Solution Features?
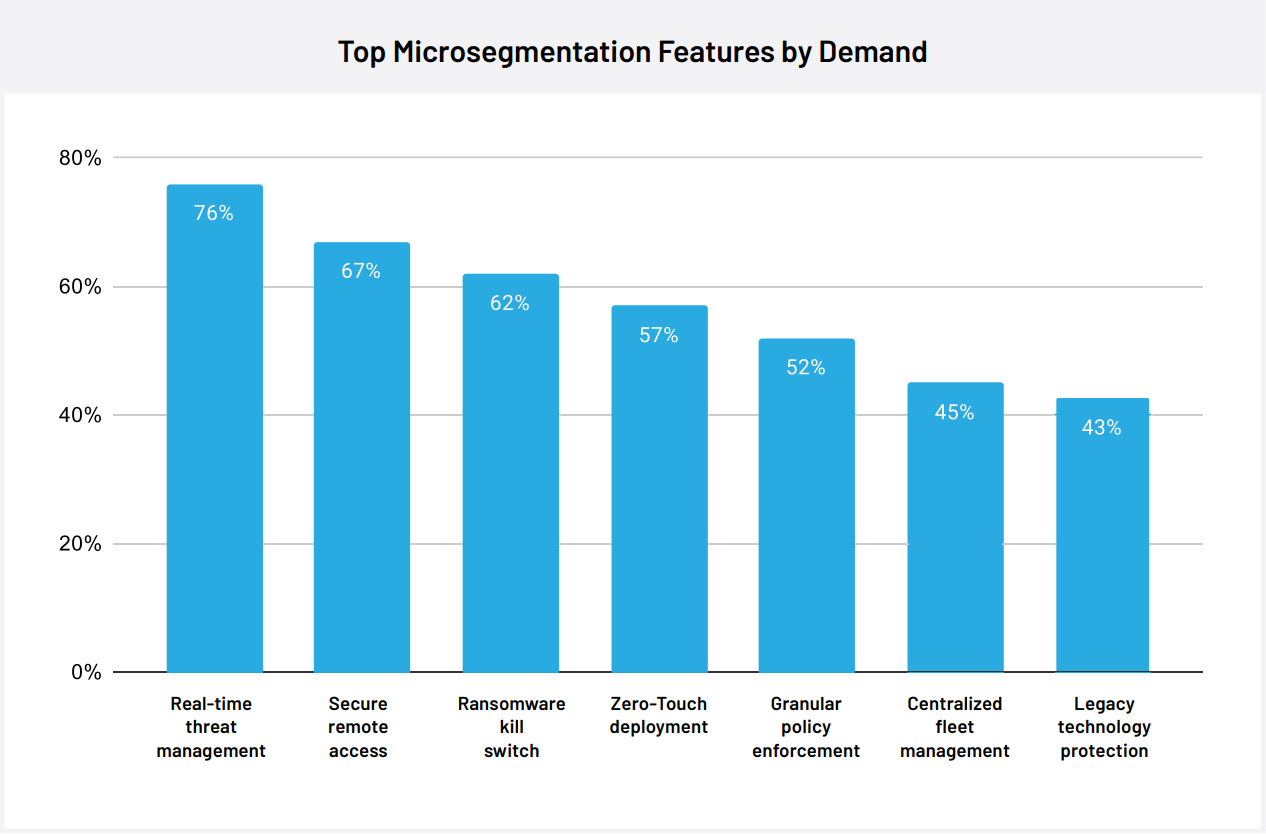
- Real-time Threat Management: 76% of cyber security leaders expect a microsegmentation solution with live threat management capabilities.
- Secure Remote Access: 67% of cyber security leaders expect a microsegmentation solution to support secure remote access.
- Ransomware Kill Switch: 62% of cyber security leaders expect a microsegmentation solution to include a kill switch functionality in case of a ransomware attack.
- Zero-Touch Deployment: 57% of cyber security leaders expect a microsegmentation solution to feature automated configuration and rollout.
- Granular Policy Enforcement: 52% of cyber security leaders expect a microsegmentation solution to enable precision policy configuration.
- Centralized Fleet Management: 52% of cyber security leaders expect a microsegmentation solution to provide a single hub for device monitoring and control.
- Legacy Technology Protection: 52% of cyber security leaders expect a microsegmentation solution to cover outdated hardware and devices.
Microsegmentation Adoption Challenges
What Are The Barriers to Adopting Microsegmentation?
Given the widespread recognition of microsegmentation, what keeps the remaining organizations from deploying the approach? While the hurdles are varied, they can be generally summarized in one word — resources:
- Insufficient Workforce: 35% of organizations that had yet to implement microsegmentation reported they lacked the people necessary to make the shift.
- Inadequate Funds: 29% of organizations that had yet to implement microsegmentation reported budgetary restrictions as a barrier.
- Limited Time: 29% of organizations that had yet to implement microsegmentation reported time was the primary constraint.

Microsegmentation Implementation
How Can Security Teams Implement Microsegmentation Right Now?
While microsegmentation has achieved consensus approval in the space, many organizations have not implemented it due to perceived difficulty. Fortunately, recent innovations in microsegmentation technology have significantly lowered — or altogether removed — these barriers.
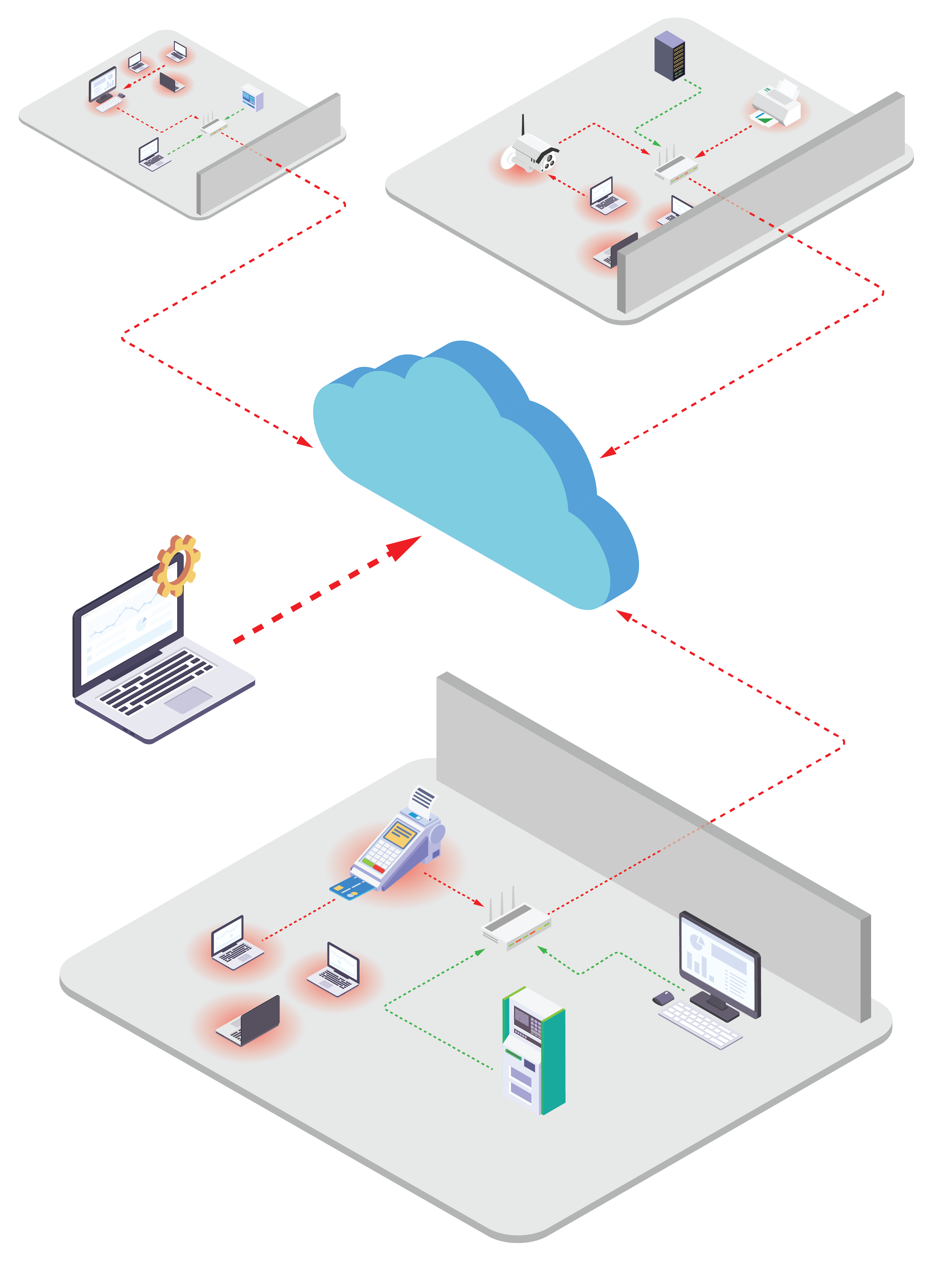
Now, organizations can implement this approach through hardware-based, plug-and-play microsegmentation solutions, like the Byos Secure Endpoint Edge.
The Byos Secure Edge is easy to deploy, and with two different form factors for different use cases, it can deliver microsegmentation to every endpoint in your fleet. The Secure Endpoint Edge is a small USB device for laptops and tablets, and the Secure Gateway Edge is an IoT gateway for wired and wireless applications. The solutions are designed for network security challenges associated with distributed work and industrial IoT use cases.
- Distributed work
- The Secure Endpoint Edge makes employee devices invisible on public Wi-Fi for roaming workers. It also helps secure work-from-home collaboration by ensuring access to a private cloud for real-time peer-2-peer work.
- Industrial IoT use cases
- The Secure Gateway Edge provides security and access for ICS/OT assets, legacy equipment, and IoT devices. This enables security teams to isolate, control, and manage devices at the edge.
In addition to security at the edge, Byos enables centralized fleet management for simple security policy provisioning, while also giving secure remote access to assets in multi-site networks in a Zero Trust fashion.
Designed to address the varied needs of cybersecurity teams worldwide, the Byos Secure Edge can help any organization implement microsegmentation on their network. Want to know more? Read the FAQ or get in touch.


