Malware Protection: How to Build the Ideal Tech Stack in 2023

Organizations dealt with 5.4 billion malware attacks in 2021, making it the second-most popular attack vector used by cybercriminals that year. While the threat of malware is high, security teams can improve their organizations’ security posture by implementing a comprehensive malware protection strategy.
From the top technologies to employee education, this article will give you an overview of current best practices.
Jump to a section…
What Is Malware Protection? Beating the Cyber Kill Chain
Building a Malware Protection Stack: Preventing Compromise
Building a Malware Protection Stack: Mitigating Threats Post-Compromise
Deploying Effective Malware Protection
"Hang on, where's Zero Trust?" you may be asking. While an important part of modern cybersecurity, Zero Trust may not be the one-size-fits-all solution some have so boldly claimed. Watch our on-demand webinar to learn more:

For more on ensuring your network security, check out our guide, Malware Protection: Everything IT Pros Need to Know.
What Is Malware Protection? Beating the Cyber Kill Chain
Organizations leverage many complementary cybersecurity solutions to prevent malware compromises from occurring and mitigate the damage when they do. To ensure they can build an effective malware protection tech stack, security teams need to create a security strategy that can prevent and respond to six of seven stages of the cyber kill chain:
- Reconnaissance: The attacker scopes the target organization and decides on the attack vector.
- Intrusion: The attacker compromises the target organization via the attack vector.
- Exploitation: The attacker deepens their access to the target organization’s network.
- Privilege escalation: The attacker improves access by achieving admin privileges.
- Lateral movement: The attacker moves from system to system across the organization’s network.
- Command and control: The attacker gains network access.
- Actions on objectives: The attacker carries out their intended goal, which could include destroying valuable information, encrypting data, etc.
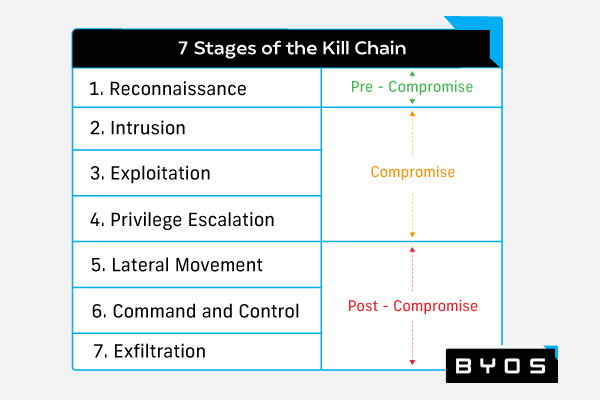
Stages two through four are grouped within the compromise phase, and security teams need to use a number of different prevention solutions to provide protection during this phase. Stages five through seven are grouped within the post-compromise phase, and security teams need to use a variety of compromise containment and mitigation technologies to respond to attacks during this latter phase.
Building a Malware Protection Stack: Preventing Compromise
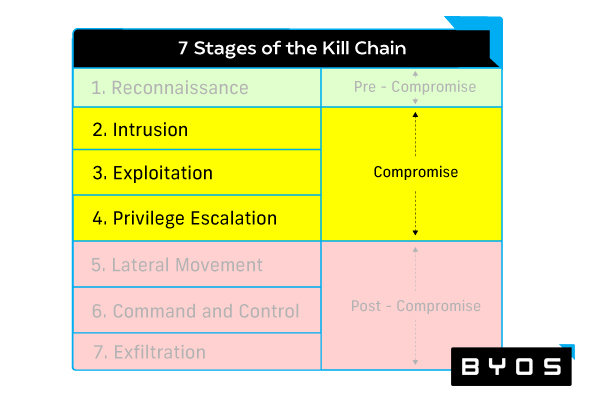
There are five main categories of malware protection solutions that security teams should deploy to help prevent compromise: vulnerability management, secure access service edge (SASE), identity management, and endpoint security. Let us explore how each of these solutions reduces the threat of a malware attack.
- Vulnerability management: Security teams can significantly reduce the likelihood that their organization will fall prey to a malware attack if they employ vulnerability management solutions. These tools help to map attack vectors on your network, rank vulnerabilities according to risk, and generate recommendations for mitigating the vulnerabilities.
- SASE: The heir apparent to classic perimeter security, SASE is a unified, cloud-based security solution that covers both networking and network security. SASE delivers services like wide area network (WAN) security, domain name system (DNS) protection, firewall as a service (FWaaS), and sometimes also includes Zero Trust Network Access (ZTNA) in one solution. This new approach can help cybersecurity teams consolidate and streamline their security architecture.
- Identity management: Supplying precision control of company resource access, identity management solutions can prevent attackers from gaining deeper system access during the compromise phase. The effectiveness of these solutions has made them an increasingly important part of the malware protection stack. In fact, recent surveys have shown that over 90% of organizations will increase their identity and access management (IAM) spending in the next few years.
- Endpoint security: According to research by the Ponemon Institute, 68% of organizations experienced an endpoint attack that resulted in data or system compromise in 2020. To help guard against endpoint compromise, security teams should invest in an endpoint detection and response (EDR) solution, an extended detection and response (XDR) solution, or bring a managed detection and response (MDR) provider on board.
Building a Malware Protection Stack: Mitigating Threats Post-Compromise
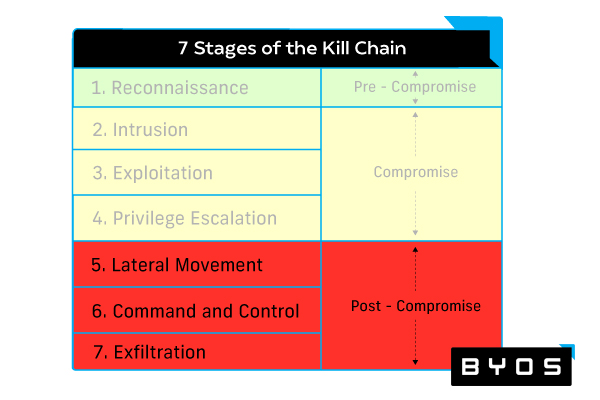
Teams should integrate three core malware protection solutions into their security architecture to mitigate damage post-compromise. These solution categories are cyber monitoring and analytics, microsegmentation, and web access protection. Let us unpack how each plays a role.
- Cyber monitoring and analytics: According to a recent survey by Statista, the median period between compromise and detection was 11 days — meaning that the attackers frequently have around two weeks to explore a penetrated system and carry out their objectives. To ensure they can stop an attack as soon as possible, security teams should incorporate a security information and event management (SIEM) solution outfitted with user and entity behavior analytics (UEBA). These cyber monitoring and analytics tools are capable of combing through vast qualities of activity data across your entire organization to quickly surface threats.
- Microsegmentation: Research by VMware Carbon Black has shown that malicious actors use lateral movement in 70% of cyber attacks, making the technique a fundamental part of the toolkit. Microsegmentation solutions reduce the broader network into individually protected and controlled microsegments — significantly reducing the ability of attackers to move laterally as a means of deepening their foothold post-compromise. These solutions give security teams direct line of sight into and control over network endpoints, allowing them to detect a compromised endpoint early and lock it down remotely.
- Web access protection: There were over four billion web application attacks in 2020, making web access protection tools like secure web gateways (SWG) and cloud access security brokers (CASB) an even more essential part of the malware protection solution stack. From blocking harmful internet content to detecting malicious actors pretending to be authorized users, these solutions ensure organizations can neutralize cloud application attacks and more before they snowball.
Deploying Effective Malware Protection
This article has explained how to protect your computer from malware via a robust and deep security stack. While every piece of this security architecture is important, some — like microsegmentation — have an outsized impact on an organization’s security posture.
Byos has created a microsegmentation solution that helps security teams maximize their ability to contain malware attacks, mitigate their damage, and remediate the incident: the Byos µGateway. Ready to learn more? Get in touch with us here.
