What Is Lateral Movement in Network Security?
Cyber attacks have become increasingly common because the tools that attackers use are now more powerful and more available through black markets. While security professionals direct considerable amounts of attention toward preventing those attacks from happening, attackers are much more focused on everything that occurs after the initial compromise.
Once attackers gain access to the network, they often move deeper into its architecture in search of valuable and sensitive data to sell at a high price, or ransom back to the organization, for example. Infections that spread throughout a network can be understood as lateral movement since attackers move freely east-west between compromised networks, devices, and applications. For organizations that have distributed workforces or rely on IoT and legacy computing devices, lateral movement tactics are a high-priority threat.
In this article, we’ll explore a working definition of lateral movement in security, key elements of this tactic, and what you can do to detect and prevent it in your network.
Jump to a section...
How lateral movement works, step-by-step
How to detect and prevent lateral movement
What is lateral movement?
Lateral movement describes the specific techniques that attackers use to explore the network, find additional resources (like apps and devices), and gain access to sensitive and valuable data. Once they’ve gained access to a network, attackers use lateral movement to maintain access, increase their privileges, and avoid detection all at the same time. Moving sideways within the network allows attackers to search far and wide for high-value information since recognizing a breach or identifying the first infected endpoint still puts network administrators far removed from the constantly escalating attack.
How lateral movement works, step-by-step
After gaining a foothold in the network, an attacker may impersonate the true endpoint user or device owner by scraping credentials in order to move to a new system in the network and adopt a new user identity. Attackers can replicate this process as they move from system to system, escalating access privileges until they find the intended payload. But the planning that goes into a lateral movement attack begins long before the initial breach itself. Here are the four main steps of lateral movement:
Step #1 of lateral movement: Reconnaissance
The internal reconnaissance phase is a prerequisite step for lateral movement itself; it allows attackers to get familiar with the inner workings of their target’s network by observing legitimate users and devices and exploring the network to map out its architecture. Reconnaissance is when attackers study network hierarchies, determine hosts’ naming conventions, and identify high-value data assets. This step sets up attackers with the intelligence they need to make informed moves during the attack, reducing the time required to locate the payload and further reducing the likelihood of detection.
Step #2 of lateral movement: Disable Security Tools
While examining network architecture, attackers can also check for existing security tools running on the network, a process that today’s security researchers have largely automated. By unhooking Anti-Virus and Endpoint Detection and Response software, attackers are able to effectively disable those solutions. AVs and EDRs work by “hooking” into application functions upon installation in order to intercept and inspect each API call for malicious intent. The unhooking process returns the code to its original state, making it impossible for the security software to do its job and allowing the attacker to avoid detection and persist in the network.
Step #3 of lateral movement: Credentials & Privileges
There are a few other ways attackers can move laterally through a network without being caught, like obtaining credentials from legitimate network users. There are many different ways bad actors can access valid credentials, including executing brute force attacks and deploying tools like keyloggers and protocol analyzers. Social engineering is also a common method for stealing login credentials; phishing attacks and typosquatting can help convince legitimate users to share their credentials willingly. When attackers use those types of illegal means to obtain the credentials that grant them network privileges, the process is often called credential dumping.
Step #4 of lateral movement: Gaining & Escalating Access
Armed with a robust map of the target network and a collection of credentials, attackers can move freely from endpoint to endpoint. Lateral movement allows them to move deeper into the network, repeating the internal reconnaissance and privilege escalation steps until the attack is complete. Attackers use this cyclical process to maintain their network access, working hard to avoid detection by studying legitimate users and devices within the network before moving laterally to infiltrate the next device or application on their way to the payload.
How to detect and prevent lateral movement
It’s easy to mistake malicious activity for regular traffic while it’s using what appear to be legitimate credentials to move side-to-side throughout a network. That’s one of the reasons lateral movement is so difficult to detect. But with a strong security solution, IT professionals can detect and remediate attacks before significant damage is done. Here are a few key strategies security teams should implement to keep networks as secure as possible:
- Audit your security hygiene: It should go without saying, but eliminating IT vulnerabilities is one of the most basic ways to protect against lateral movement. Regularly updating software, isolating unpatched systems, maintaining unique passwords, and restricting network communications are all smart ways to improve your security hygiene. Maintaining a robust security posture demands that every user, application, and endpoint is running up-to-date software and using the most advanced and effective technologies available for any given task or purpose.
- Develop internal network intelligence: Developing a detailed picture of login patterns for each user and device on a network is a good way to make rogue usage stand out as a potential threat. With this internal network intelligence, only the traffic that lands outside the typical patterns of behavior will trigger credential abuse alerts. That helps combat alert fatigue, which is when security professionals have a harder time noticing and reacting to actual threats because they are overwhelmed by the overabundance of mundane, harmless alerts.
- Assess your endpoint security: In today’s world, more and more devices are connecting to corporate networks remotely, without plugging into the corporate network directly. Increasing your security team’s visibility into endpoints like laptops and mobile devices will lead to a better understanding of normal activity and login patterns, making it that much easier to protect remote devices from threats and detect breaches at a distance. Securing each individual endpoint will increase your ability to prevent, detect, and respond to attacks, no matter where the breached device is located.
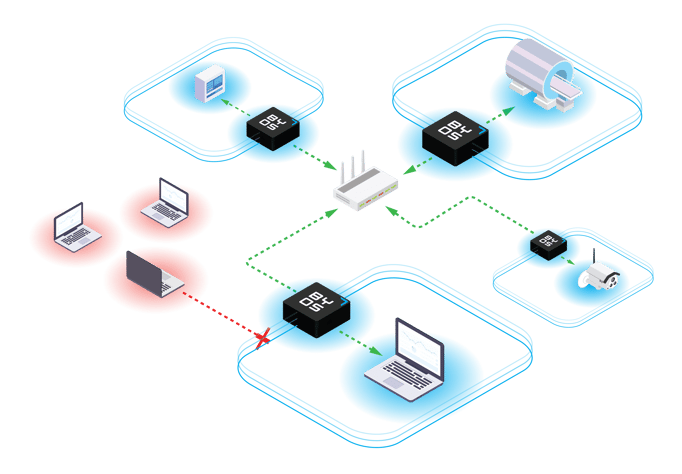
- Implement edge microsegmentation: One of the primary ways to detect and prevent lateral movement is with edge microsegmentation. By dividing networks into distinct granular zones, edge microsegmentation allows for protection of every individual endpoint. This decreases risk by reducing the available attack surface, while simultaneously making containment and remediation easier if security incidents do occur.
As attackers advance in their effectiveness and sophistication, security experts have a finite window of opportunity in which they can effectively detect and remediate threats. That window, called breakout time, refers to the time it takes from the initial compromise to the beginning of lateral movement. Once lateral movement begins it can be extremely difficult to detect and even harder to remediate. That’s why breakout time is so limited, as opposed to lasting from the initial breach to attack completion.
Breakout times are getting shorter and shorter; in 2019, the average window was approximately nine hours. In 2020, it shrank to four hours and 28 minutes. Today, security experts face an average breakout time of one hour and 58 minutes, requiring them to detect, investigate, and remediate or contain a threat in under two hours.
Two hours may not seem like a lot, but Byos is dedicated to protecting distributed and remotely accessible corporate networks from all kinds of cyberattacks, including APTs and lateral movement threats. The patented Byos Secure Gateway secures every single endpoint, protecting your organization’s employees no matter what device they’re using or where they are when they connect to your network. Ready to learn more? Speak with us here.

