Turning the Tables on Bad Actors' Reconnaissance & Discovery Practices
Editor’s Note: The purpose of this paper is to illustrate how the MITRE ATT&CK framework reveals adversaries’ attack chains so that we can identify the “choke points” - those places in the attack process through which adversaries must go, and becomes a place where defenders can put ourselves in a position of power. This approach focuses on where we can have confidence that, despite a bad actor successfully completing one step in their campaign, we can bring an attack to a complete halt.. Using the discovery and reconnaissance stages of the MITRE ATT&CK framework is the ideal illustration where we can demonstrate that strategy.
Introduction
-
Overview of the Discovery and Reconnaissance tactics in the MITRE ATT&CK framework
-
Importance and relevance of these tactics from the attackers' perspective
Tactics and Techniques
-
Where Discovery and Reconnaissance tactics fit in the attack flow
-
Common methods used by attackers before, during, and after these stages
-
Categorizing the various techniques into categories like network, email, devices, cloud, credentials, etc.
Detection and Prevention
-
Methods of detecting activity in the Discovery and Reconnaissance stages
-
Preventative measures organizations can take
-
Best practices to prevent, detect and remediate
-
Technologies cyber leaders can use to help them defend against these techniques
Conclusion
Epilogue: What are the Characteristics of Technologies that Truly Prevent Attack Tactics?
Introduction
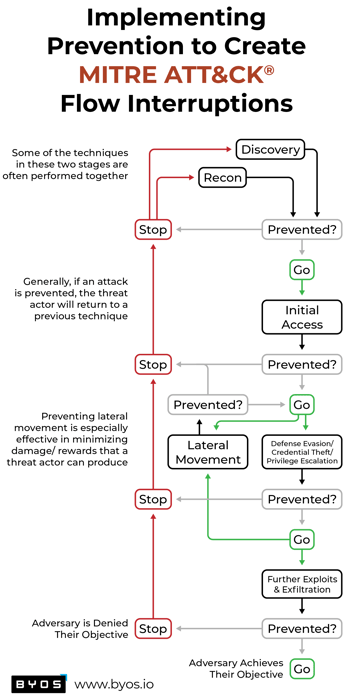
A popular metaphor for using the MITRE ATT&CK Framework to build a cyber defense strategy is the chess strategy of “sacrificing a pawn to save the queen”. If you are new to the MITRE ATT&CK Framework, upon completing this article, you will better understand how to focus your security architecture by channeling your investments in time, people, and capital into what more effectively prevents adversaries from reaching their endgame.
The flow of adversaries’ attacks have become increasingly sophisticated. Let’s begin by focusing on two tactics used by attackers early in their campaigns. Reconnaissance, where all attack campaigns begin, and Discovery play a significant role in the attack plan, but other stages in the campaign are more effective and easier for us to defend.
That is because there are limited ways to detect or prevent many of the techniques in these two stages because the attackers’ activities are: 1) outside the organization’s control, 2) easily disguised, or 3) passive. Of course, there are some exceptions, so it’s important to drill down into the specific adversary tactics to know which ones play a more important role in interrupting the attackers’ campaigns.
Attackers use these stages to gather information about their target, to identify potential vulnerabilities, and to develop their campaign strategy. These stages, when combined with gaining initial access and being able to move around the network freely, are a critical factor in making a determination if or how aggressive a target will be pursued. Understanding these tactics and their impact is crucial for cybersecurity professionals to protect their organizations from attacks.
Tactics and Techniques
Reconnaissance and Discovery tactics are used by attackers to gather information about the target organization and its users and technologies, to identify vulnerabilities, and to plan their attack strategy. These tactics are often used in the early stages of an attack, and attackers may return to these stages throughout the attack to gather additional information.
During the Reconnaissance stage, attackers learn about the target organization's infrastructure and systems. This may involve gathering information about the target's domain names, IP addresses, email addresses, and user accounts. Attackers may also use phishing techniques to obtain credentials or deploy malware to gather information.
During the Discovery stage, attackers attempt to identify assets and resources within the target organization. This may involve network mapping, port scanning, and service enumeration. Attackers may also use open-source intelligence (OSINT) techniques, such as searching for information about the organization on social media platforms, job postings, and public records.
Analysis - How to reduce the impact of Reconnaissance Tactics
The Reconnaissance process is generally the first step where threat actors build their plan. The Discovery phase comes later when access has been established in an asset (or assets) that opens the door inside the network. During an attack campaign, attackers will return to these two stages.
Of the 10 attack techniques in this category, many cannot be easily mitigated because much of the information is publicly available or is available using OSINT tools and techniques. The good news is that information is only good if it can be put to good use. So the solution is to interrupt the information acquired during this phase to be used in other attack vectors.
In the MITRE ATT&CK Framework, Reconnaissance techniques and their mitigation methods are shown in this chart:
|
Reconnaissance Technique |
Challenge |
Attack Vector Preventing Further Progress by Attackers |
||
|
Initial |
Lateral |
Privilege |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
X |
||
|
Sources are outside the target’s control |
X |
X |
||
|
Sources are outside the target’s control |
X |
X (4/6) |
||
|
Sources are outside the target’s control |
||||
|
Sources are outside the target’s control |
||||
|
Sources are outside the target’s control |
||||
|
Sources are outside the target’s control |
||||
|
Sources are outside the target’s control |
||||
Of the 10 attack techniques, here is a quick breakdown:
-
7/10 are, for the most part out of the organizations control to protect or conceal, because information about organizations are required to be in the public domain for the business to operate. For the entire ATT&CK framework, investing in the mitigation and detection of this activity provides the least value.
-
3/10 can often be detected by endpoint or network tools (EDR/MDR/XDR/SIEM/UEBA)
-
5/10 detection-dependent protections can be supplemented with prevention technology.
(Caution: Prevention technology may not be what is claimed, as many vendors use the term improperly. For instance, bad actors have developed ways to bypass MFA, while passwordless and hardware-based technologies have the attributes of true prevention. A discussion of this is covered at the end of this paper.)
Analysis - How to reduce the impact of Discovery Tactics
In the MITRE ATT&CK Framework, Discovery attack techniques and their mitigation methods are shown in this chart:
|
Discovery Technique |
Challenge |
Attack Vector Preventing Further Progress by Attackers |
||
|
Initial |
Lateral |
Privilege |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
|||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
X |
||
|
Reliable detection & user behavior |
X |
|||
|
SASE/SSE/CASB protected |
X |
|||
|
SASE/SSE/CASB protected |
X |
|||
|
SASE/SSE/CASB protected |
X |
|||
|
SASE/SSE/CASB protected |
X |
|||
|
SASE/SSE/CASB protected |
X |
|||
Of the 30 attack techniques in this category, here is a quick breakdown:
-
25/30 can often be detected by endpoint or network tools (EDR/MDR/XDR/SIEM/UEBA), but evasions to detection are being developed by threat actors at an accelerated pace.
-
Of the 22 of 25 detectable techniques, prevention technology can be applied to of those techniques as well, which provides significant advantage to interrupting an adversary’s progress.
-
5/30 can be prevented or largely enforced by well-defined protections in OSI Model Layers 6 & 7. SASE/SSE tools that implement zero trust principles (such as role-based “deny by default” policy enforcement)
From the charts above, some pretty evident conclusions can be drawn.
-
Technology that can cloak devices, prevent most initial access, and minimize lateral movement can circumvent the majority of discovery & reconnaissance techniques. The key focus is to prevent an adversary from gaining any initial foothold, and when they do find a hole, to keep the blast radius as small as possible by limiting their ability to discover or access other devices.
-
Protecting credentials and access privileges is another key to limiting the damage a threat actor can do. When combined with anti-phishing and anti-malware detection technologies, passwordless technologies (such as Auth0 and HYPR) and FIDO hardware authentication keys (such as Yubikey and Thales) can thwart most common phishing campaigns, file access, and other forms of accessing machine information.
-
A combination of just the right network/endpoint protection, SASE/SSE, passwordless and FIDO technologies can PREVENT 95% of attack flows that threat actors will attempt. These technologies are relatively simple to design, deploy, and maintain compared to the complex and ineffective tools of the past. For instance, the best-in-class tools on the market today that address network/endpoint and SASE/SSE protections can replace the 6-14 tools that would have been required to be integrated in the past. To learn more about how Byos plays a unique role to fill the gaps that no other technology can address, click here to learn more.
These tactics enable attackers to gather information about the target organization, identify potential vulnerabilities and plan their attack strategy. Understanding how these tactics are performed and their impact on the rest of the 12 attack flow stages serve to develop the controls, processes, and technologies that will interrupt attackers from continuing through their attack chain to the completion of their goal(s).
(Authors note: There is another attack stage defined in the MITRE ATT&CK framework called “Resource Development” which is similar to Discovery and Reconnaissance. It is not covered in this paper, because the attacks are less likely to be effective when the proper controls preventing initial access and lateral movement with edge security and absolute least privilege restrictions are in place.)
Description of Discovery Techniques
In this section we provide descriptions of what specific Discovery techniques are, and tools that cybersecurity experts have familiarity, so that a deeper understanding of the charts above can be developed by readers who wish to gain deeper insight into where and why preventions and detections can, or cannot, be effective. Detecting and preventing attacks that utilize Discovery and Reconnaissance tactics requires multi-layered defenses that include technical controls, processes, and user awareness.
Below, is a brief synopsis of each of the techniques attackers use during the Discovery phase, along with widely available tools used for each. Similar techniques for the Reconnaissance stage can be acquired from the MITRE site here.
-
Active Scanning (T1595) probes target networks to identify open ports and services for vulnerabilities to exploit. Common tools used include Nmap, Nessus, OpenVAS, Qualys. Perform network traffic monitoring, IDS/IPS, and log analysis.
-
Gather Victim Host Information (T1592) searches for hosts to identify vulnerabilities and potential targets. Common tools used include whois, DNS enumeration, ping sweeps. Perform network traffic monitoring, IDS/IPS, and log analysis.
-
Phishing for Information (T1598) sends targeted phishing emails to collect information such as usernames, passwords, and other credentials. Common tools used include Social engineering tactics, phishing kits. Perform user education and awareness training, email filters, content scanning, link analysis, etc.
-
Gather Victim Identity Information (T1589) searches for employees to carry out social engineering attacks and gain access to sensitive information. Common sources used include Social media, online profiles, job postings. Perform employee education and awareness training, network traffic monitoring, and log analysis.
-
Gather Victim Network Information (T1590) searches for network infrastructure to identify vulnerabilities and potential targets. Common tools used include Network mapping tools, network scanning tools. Perform network traffic monitoring, IDS/IPS, and log analysis.
-
Gather Victim Org Information (T1591) searches organization, partners, vendors, & customers to identify vulnerabilities and potential targets. Common tools used include public records, online profiles. Perform network traffic monitoring, and log analysis.
-
Search Closed Sources (T1597) searches sources that require authentication or are not publicly accessible. Common tools used include Stolen credentials, password cracking tools. Perform user education and awareness training, monitoring of failed login attempts and password cracking attempts, and log analysis.
-
Search Open Technical Databases (T1596) searches publicly available databases and repositories. Common sources used include Shodan, Censys, Google Dorks. Perform network traffic monitoring, and log analysis.
-
Search Open Websites/Domains (T1593) searches open-source websites and domains, such as social media and job postings. Common tools used include Google, LinkedIn, Facebook, Twitter, GitHub, and Pastebin. Monitor network traffic to known malicious domains/IPs, excessive abnormal traffic. Monitor public websites and social media.
-
Search Victim-Owned Websites (T1594) searches websites owned by the organization or employees, such as blogs, forums, & personal websites. Common sources used include Google, Bing, and Wayback Machine. Monitor unauthorized access, unauthorized modifications, or unusual activity on websites, and outbound connections to suspicious domains/IPs.
Note: The Reconnaissance Stage is much more extensive yet the adversary and defense tactics are similar, so we have provided a link below to the length of this paper from growing too long.
Choosing the Appropriate Focus on Detection and Prevention
Detecting Reconnaissance tactics is a necessary part of a layered defense, but it has a number of drawbacks when compared to prevention.
- Threat actors have become extremely proficient at evading detection.
- Detection requires that an event has already occurred in order for it to be detected.
- An event that never happens is better than one that is stopped.
- An event that is detected and remediated can give an attacker valuable information to continue attacking.
- Sometimes, an event can be intentionally triggered by an attacker as a diversion, an evasion or misdirection in a larger campaign.
- Where prevention is not possible, the emphasis on detection should be increased.
- But, where an effective and reliable prevention method is available, that should be implemented.
- Defense-in-depth dictates that detection should always be in place.
Making Prevention Most Effective in Combating Adversaries’ Attack Campaigns
Traditional technologies that can prevent these attacks, intrusion prevention systems (IPS), firewalls, and endpoint/network cloaking and containment tools. These well-deployed technologies have a reputation for being easily bypassed by bad actors and penetration testing teams. This is not due to defects in the technologies themselves, although there are a number of CVEs being published that might cause some to belabor this point. The truth is that there are three primary reasons these older technologies don’t measure up to their promise:
-
The administrative interface designs bring a lot of baggage. That leads to policy rules that drift from their original intent and design. Changing those architectural underpinnings would cause extensive unintended consequences to their loyal customer base.
-
They are designed for a perimeter-based, single-purpose role in days-long-ago when attacks were not as sophisticated.
-
The complexity of these tools in the cybersecurity portfolio with dated integrations creates many gaps because changes in one of the technologies can improve the posture in one place while opening a hole in another place.
Newer technologies are unencumbered by “existing ways of doing things”. User interface design has advanced quite a bit over the last 3-4 years. Perimeter-less architectures have been developed with a broad understanding of the extended enterprise: mobile, BYOD, cloud, IoT, edge computing, Work-from-Anywhere, and third-party access. Innovative ways of cloaking devices and networks, true zero trust and true microsegmentation, and the rapidly evolving attack prevention are coming from startups that will become the ‘next big thing”. In this rapidly changing technology landscape, you should be looking for those technologies that can replace multiple technologies. Byos is one of those technologies that does all of the above.
Conclusion
Because you have few options to prevent so much of the information from being acquired, we must shift our strategy to preventing the acquired information from leading to success in the subsequent stages of the attack chain. So in understanding the specific methods used by attackers during the Discovery and Reconnaissance stages, you can prepare and implement strategies that reduce the likelihood of the information acquired from being used against you. And the most effective, efficient, and cost-effective means of doing that is to prevent those subsequent tactics from happening before they get started.
When other controls are in place that can interrupt the use of the data acquired during the Discovery and Reconnaissance stages, they are rendered to be less critical tactics that need to be detected in an attack sequence. By implementing effective mitigation in other stages of the attack chain, organizations will reduce the rate of adversaries’ overall success in reaching their ultimate objectives.
To improve security posture and reduce the likelihood of adversaries reaching their ultimate goals, some of the defense tactics are best built before and after the Discovery and Reconnaissance stages. These solutions can include technologies such as intrusion detection and prevention, firewalls, and EDR/MDR/MDR/SIEM. State-of-the-art defenses of note are technologies that cloak devices from being discovered or accessed, prevent lateral movement over the network,, and provide ‘absolute least privilege access controls. Regular vulnerability scans, penetration testing, red/purple exercises, and dark web monitoring help identify potential exposures where your organization’s information has been compromised or improperly exposed.
It should be clear that an emphasis on preventions does not suggest that other defensive controls should be ignored. A solid defense-in-depth strategy includes detection and response, in addition to the preventative measures we put in place. At the same time, prevention will reduce the necessary operating budget for detecting and responding.
To learn more about how Byos can help you achieve your goal preventing your adversaries from reaching their goals, connect with us on LinkedIn or use the button below to start a conversation.
Epilogue: What are the Characteristics of Technologies that Truly Prevent Attack Vectors?
Many vendors play fast and loose with the term “prevent”. For instance, one vendor made the claim that their solution prevented attacks because it was able to “detect in real time”. Obviously, nothing’s perfect. And conceivably, we would not argue that anything connected to a network has the potential to be breached. With that stated, it’s appropriate to provide the criteria that we propose need to be met:
- It cannot be bypassed, disabled, impersonated or otherwise compromised for the protections that are the technology is employed to prevent.
- It cannot be reverse engineered nor have any of it’s components accessible from being easily revealed.
- It stops an attack technique before the attack has an opportunity to start.
- It does not produce false positives.
- It must prevent both known and unknown threats.
- Fail-open is not an option. (But many situations will dictate “fail-open” to be necessary. A life-supporting medical device is a good example.)
- It’s access controls must be “default deny”.
- For any conditions outside the parameters that are known, it will deny access.
Our definition for “prevention” does not rise to the level that the likelihood of an event occurring must be mathematically impossible. But, we think a reasonable definition is that the barrier to success is so low that attackers will abandon their efforts to even try. For instance:
- If a device in all cases discards any and all IP packets from sources that are not fully trusted, then the ability of an adversary to even know that the IP address is valid would be “impossible”. The device would not even process malformed packets.
- If a user opened a malicious website, clicked on a malicious email in a link, or plugged an infected USB drive into their device; if the device were unable to send packets to any of its peers on the local network or to any device outside the local network, its ability to discover and spread to other devices would be contained. Similarly, the ability to exfiltrate information or do any other damage would be prevented.
